Essential Trends in Cyber Security Forensics for 2024

-
Content
- Introduction
- Increased Use of AI and ML in Cyber Security Forensics
- Rise of Quantum Computing Threats
- Expansion of Zero Trust Architecture
- Utilization of Generative AI in Phishing Attacks
- Emerging Trends in Incident Forensics
- Conclusion
-
Content
- Introduction
- Increased Use of AI and ML in Cyber Security Forensics
- Rise of Quantum Computing Threats
- Expansion of Zero Trust Architecture
- Utilization of Generative AI in Phishing Attacks
- Emerging Trends in Incident Forensics
- Conclusion
Introduction
In our digitally driven world, cyber security forensics stands out as a key field in the battle against cyber threats, playing a crucial role in detecting, investigating, and mitigating these dangers. As technology evolves, cyber-attacks become increasingly complex and sophisticated, highlighting the importance for those in the field to stay updated on the latest trends in digital forensics and cyber security. This area, a blend of digital forensics and cyber security, is not just about reacting to incidents but also about using cutting-edge detection methods and strategic intelligence to prevent future threats. The impact of cyber security forensics goes well beyond simply responding to incidents. It involves a holistic strategy to protect digital assets, safeguard sensitive information, and ensure the resilience of IT systems in the face of a constantly changing landscape of cyber threats and challenges. New technologies are broadening the scope of cyber security forensics, introducing innovative tools and techniques that provide a forensic edge in the cyber world. Understanding the crucial roles of digital forensics services, digital forensics software, and DFIR (Digital Forensics and Incident Response) tools is essential in strengthening the security of information infrastructures. We will delve into the current and future trends shaping the future of cyber security forensics, emphasizing the need for innovation and flexibility to navigate the challenges of the digital age.
Increased Use of AI and ML in Cyber Security Forensics
1. AI (Artificial Intelligence)
AI is set to transform the landscape of cyber security forensics, offering unparalleled capabilities in the detection, analysis, and response to cyber threats. These systems, trained on extensive datasets, have the ability to discern patterns and anomalies that might go unnoticed by human analysts. Moreover, AI-powered forensic tools excel at identifying even the most sophisticated and novel threats, including advanced persistent threats (APTs) and polymorphic malware. Thanks to their continuous learning from new data, AI algorithms are in a constant state of evolution, providing a dynamic line of defense that adapts to the ever-changing threat environment. This adaptability is essential for maintaining a strong forensic cyber security posture in a scenario where adversaries continually refine their tactics.
2. ML (Machine Learning)
Imagine Machine Learning (ML) as a super-sleuth in the realm of cyber security forensics, always on the lookout, learning from the whispers of the past to guard the future. This digital detective pores over historical data from cyber incidents like a seasoned detective revisiting old case files, seeking patterns and clues to unveil potential threats lurking in the shadows of the network. But ML isn’t just the guard it’s also the diligent assistant, taking over the routine grind of sifting through logs and gathering digital evidence, freeing the human minds to dive into the more intricate puzzles of cyber investigations. By weaving ML into the fabric of digital forensics software, the whole process transforms, becoming faster, sharper, and more responsive. It’s like equipping our cyber guardians with jetpacks, empowering them to soar above the digital landscape and respond with lightning speed to any threat that dares to surface.
Rise of Quantum Computing Threats
The arrival of quantum computing is a big deal in the world of computers, opening up new possibilities but also creating risks for online security. Think of quantum computers as super-powerful giants from ancient stories, able to solve complex problems fast, much quicker than our regular computers.
1. Cracking Encryption Codes
Quantum computers possess the capability to break widely used encryption algorithms, such as RSA and ECC, which form the backbone of digital forensics cyber security. This ability threatens to render current cryptographic standards obsolete, exposing sensitive data to unauthorized access.
2. Enhanced Cyber Attacks
Quantum computing is poised to revolutionize cyber warfare, empowering attackers with unprecedented capabilities. Its immense computational power can simplify tasks like password cracking and network infiltration, presenting new challenges. This emphasizes the crucial role of cyber security forensics in countering quantum-powered threats and safeguarding digital privacy.
3. Data Retrospective Decryption
Moreover, the strategy of capturing encrypted information now with the intent to decrypt it later, as quantum technologies evolve and become widely available, presents a significant threat to the security of data stored over the long term. This “harvest now, decrypt later” approach necessitates a proactive stance from cyber security experts.
4. Threat to Blockchain and Cryptocurrencies
Quantum computing poses a formidable challenge to the cryptographic bedrock upon which blockchain technologies and cryptocurrencies stand. With the power to unravel these cryptographic defences, quantum capabilities could usher in an era of heightened vulnerability, exposing digital assets to theft and fraudulent activities.
5. Disruption of Digital Trust Systems
Moreover, the very foundation of digital trust mechanisms, such as digital signatures and certificates, is at risk in the face of quantum advancements. The potential for quantum computers to compromise these trust systems threatens to erode confidence in digital transactions and communications. Addressing these quantum-induced vulnerabilities is a critical mission for the cyber security forensics community, demanding a forward-looking approach to cryptographic techniques capable of standing firm against the quantum computing challenge.
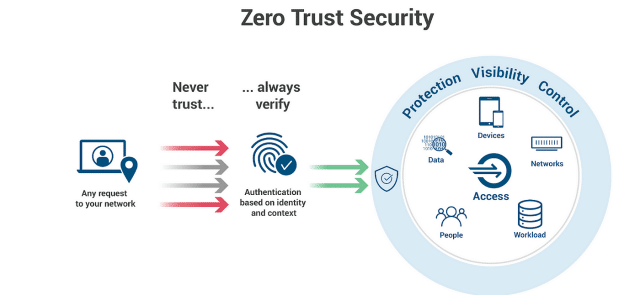
Expansion of Zero Trust Architecture
The rise of Zero Trust Architecture marks a transformative approach in cyber security forensics, emphasizing proactive and dynamic defences to shield digital realms from both outside and inside threats. Let’s explore the key elements and implications of Zero Trust Architecture within the cyber security forensics landscape.
1. Micro-Segmentation
At the core of Zero Trust Architecture, you’ll find micro-segmentation, a strategy that breaks down networks into smaller, more controllable segments. This division not only strengthens digital forensics by confining potential security breaches to limited areas, thereby curbing the attackers’ ability to move sideways across the network but also sharpens the focus for cyber security forensic teams.
2. Multi-Factor Authentication (MFA)
Integral to Zero Trust’s defence strategy is the implementation of Multi-Factor Authentication (MFA), which serves as a critical checkpoint to affirm the identities of users and devices attempting network access. In the realm of digital forensics and cyber security, MFA emerges as a vital defence mechanism against unauthorized entry, especially in scenarios involving stolen credentials or phishing schemes.
3. Least Privilege Access
The principle of least privilege access is a fundamental aspect of Zero Trust Architecture, ensuring that individuals and devices obtain only the essential level of access needed for their tasks. This strategy effectively minimizes cyber attacks, thereby constraining the potential fallout from security breaches. For professionals in cyber security forensics, the implementation of least privilege access streamlines the monitoring of user actions and the detection of unusual patterns, facilitating more efficient forensic investigations and enhancing overall data protection.
4. Continuous Monitoring and Analytics
Zero Trust Architecture underscores the critical need for ongoing surveillance and analytics to pre-emptively identify and counteract threats. This vigilant approach is indispensable in cyber security forensics, as it allows analysts to quickly spot and address security incidents, potentially stopping them in their tracks. The deployment of sophisticated analytics tools, fuelled by artificial intelligence (AI) and machine learning (ML), is central to this effort, enabling the examination of extensive data sets to detect irregularities and signs of cyber threats.
Utilization of Generative AI in Phishing Attacks
The emergence of Generative AI technologies marks a transformative moment in cyber security forensics, especially concerning phishing attacks. This segment delves into how Generative AI is reshaping phishing tactics and the ensuing challenges for cyber security forensics practitioners.
1. Creation of Convincing Fake Content
Generative AI’s prowess in creating text, imagery, and video content that closely mimics genuine material positions it as a potent instrument for concocting phishing communications that appear legitimate. Leveraging AI, these deceitful messages and emails are customized for specific individuals, drawing on publicly accessible data or information from past data breaches.
2. Personalization at Scale
One of the most formidable challenges presented by Generative AI in phishing scenarios is its capability to personalize attacks on a massive scale through automation. By analysing extensive data sets, cyber criminals can use AI to pinpoint potential targets and tailor phishing messages to match their interests, habits, and ways of communicating.This complexity adds to the workload of cyber security forensics professionals, who already face the tough job of educating users and reducing risk exposure.
3. Evasion of Detection Tools
The content generated by AI for phishing purposes can adapt over time, eluding static defense strategies. This calls for a more flexible and evolving approach to digital forensics and threat identification. Cyber security forensics teams are thus compelled to incorporate cutting-edge AI and ML technologies into their defense mechanisms to keep pace with the continuously shifting threat landscape driven by AI.
Emerging Trends in Incident Forensics
As we step into 2024, the cyber security forensics landscape is undergoing rapid transformation, fueled by technological progress and evolving cyber threats. Here are four insights into the emerging challenges and trends in incident forensics:
1. Increasing Complexity of Cyber Attacks
The sophistication of cyber attacks is on the rise, with perpetrators now utilizing advanced technologies like AI and machine learning to slip past defensive measures. This escalation demands a more intricate approach in cyber security forensics, where traditional investigative techniques merge with sophisticated analytical tools. This blend is essential for peeling back the layers of complex cyber threats and understanding their mechanisms and origins.
2. Integration of Big Data Analytics
The vast amount of data generated in cyber incidents necessitates the adoption of big data analytics within cyber security forensics. The application of big data techniques enables forensic experts to efficiently navigate through extensive datasets. This approach is crucial for spotting trends and irregularities that might reveal the tactics or sources of information security, providing a clearer path to resolution and prevention.
3. Emphasis on Proactive Forensics
The shift towards proactive forensics marks a significant evolution in the field, with cyber security professionals now taking the initiative to seek out potential threats lurking within their systems, rather than adopting a reactive posture post-incident. This proactive approach facilitates the early identification and neutralization of threats, effectively reducing their potential impact on organizations. By staying one step ahead, forensic teams can ensure better preparedness and resilience against cyber threats.
4. Rise of Cyber Forensics as a Service (CFaaS)
The growing need for specialized forensic skills has led to the rise of Cyber Forensics as a Service (CFaaS), a model that offers organizations the flexibility to engage expert forensic services on demand. This approach allows for scalable access to advanced forensic tools and expertise without the need for in-house capabilities, making cutting-edge forensic investigation accessible to a wider range of organizations. As cyber threats continue to evolve, CFaaS provides a dynamic and adaptable solution to meet the complex demands of modern cyber security forensics.
Conclusion
Navigating the intricate and ever-changing landscape of cyber security forensics underscores its pivotal role in defending against cyber threats. The array of emerging trends we’ve traversed from AI and ML’s growing influence, the spectre of quantum computing, the strategic shift towards Zero Trust Architecture, to the cunning use of Generative AI in phishing, and the latest in incident forensics reveals the fluid and complex nature of cyber threats. This journey underscores the essential, proactive, and innovative role of cyber security forensics in shaping organizational security in an era where digital threats are increasingly cunning. This exploration acts as a vital call to action for organizations to enhance their digital forensics capabilities, embrace forensic services, and incorporate the latest forensic tools and DFIR (Digital Forensics and Incident Response) technologies. To sum up, evolving cyber security forensics strategies to counter emerging threats is imperative for those tasked with protecting our digital domains. As we look forward to 2024 and beyond, the cyber security forensics field continues to stand as a pillar of innovation, resilience, and alertness, committed to securing the digital valuables and privacy of both individuals and enterprises globally.