
An important role of Database Forensics
Databases are the fundamentals of the current software applications which contain completed data that might be the crucial clues to disclose the truth, and important evidence to identify the crime. But database operator is required to have strong technical knowledge or background in database so this software is exactly helpful for user who is not senior in this filed. With our product, the user can acquire the underlying data from the database files more easily in a forensically sound manner, and bypass the password of the regarding application. Get close to the crime clues.


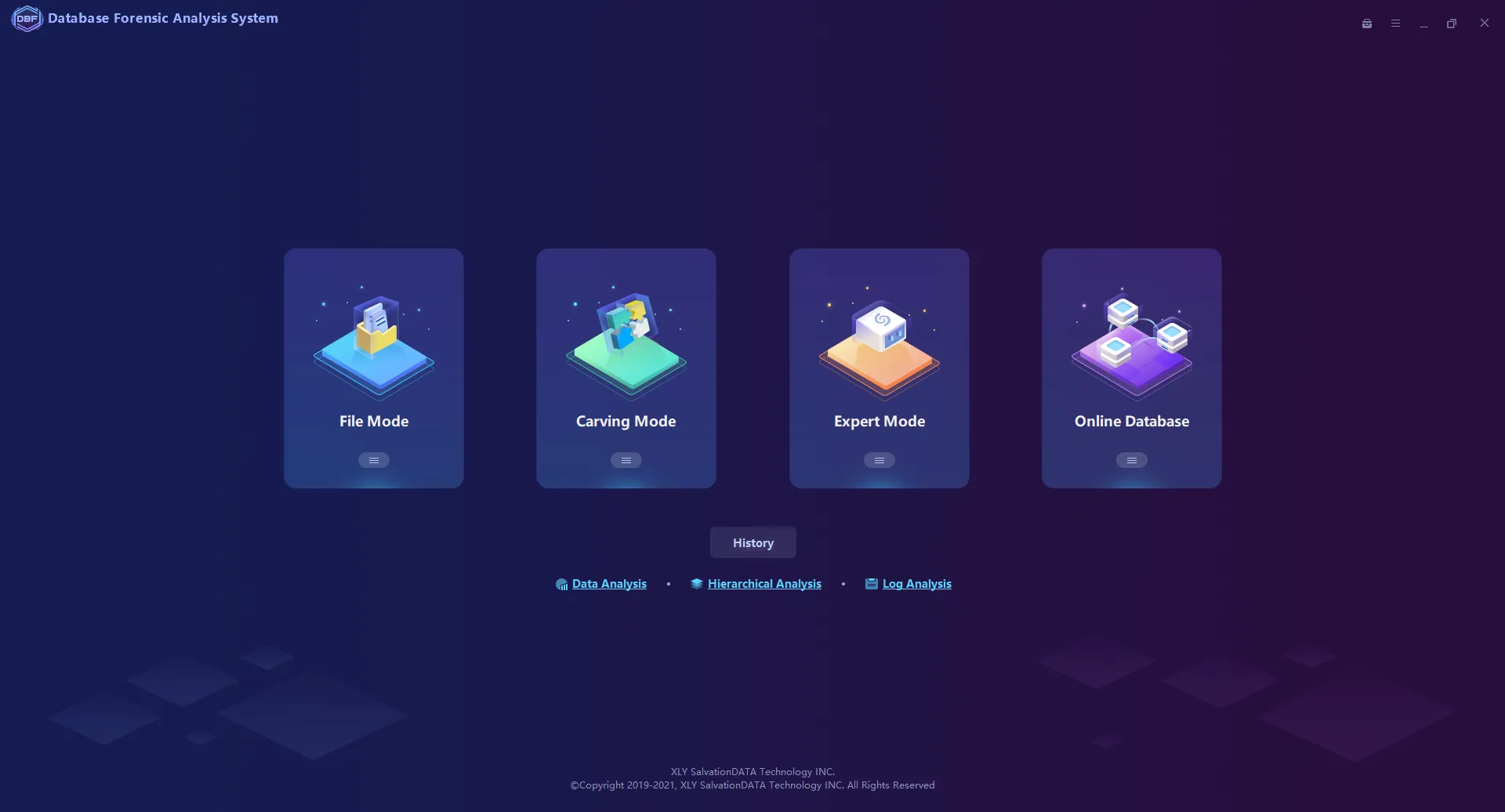
Database Forensic Analysis System
Unrestricted Accessibility to the database files no need for password & account info from the application system or pre-configuration of regarding database environment.
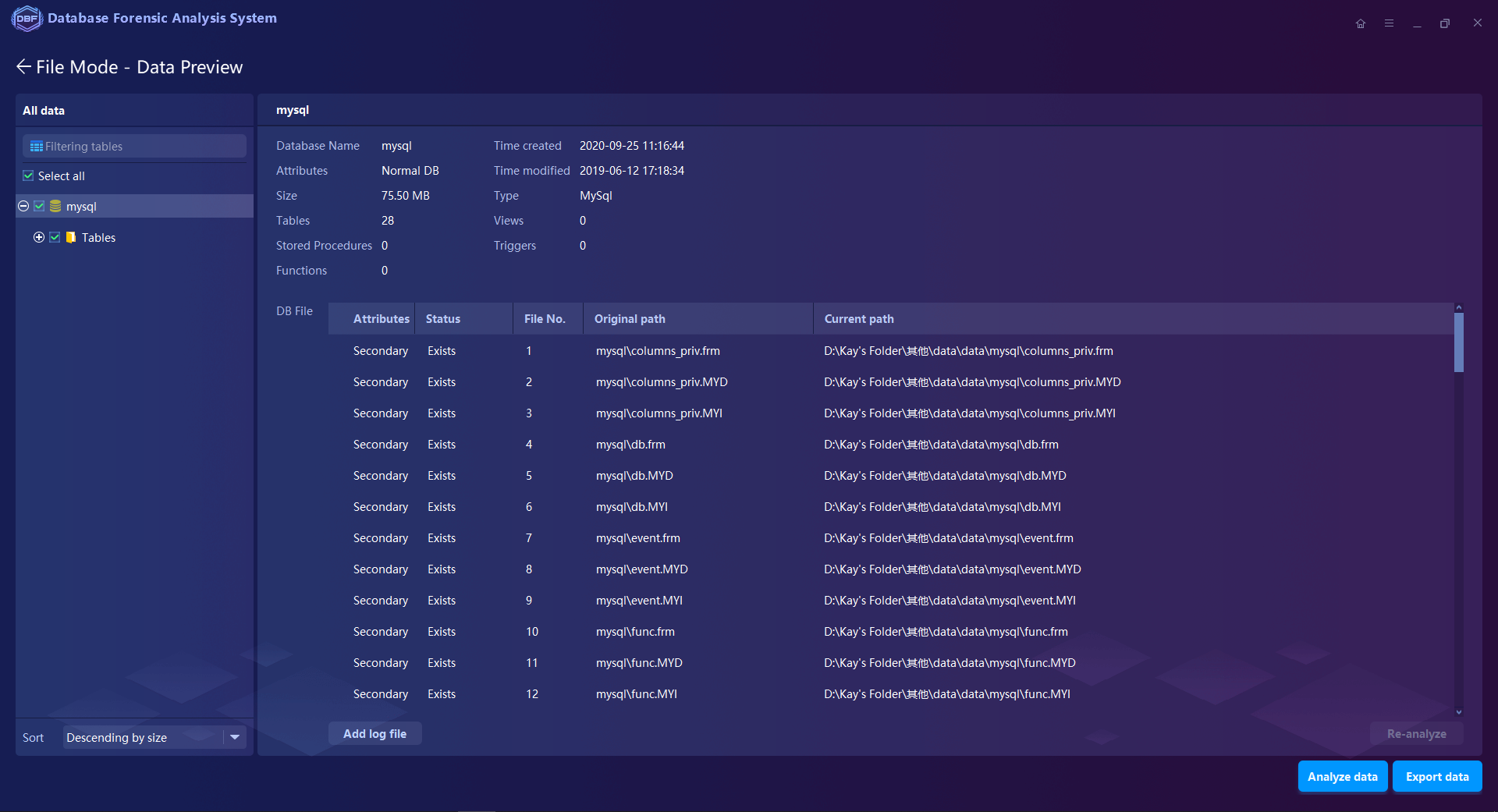
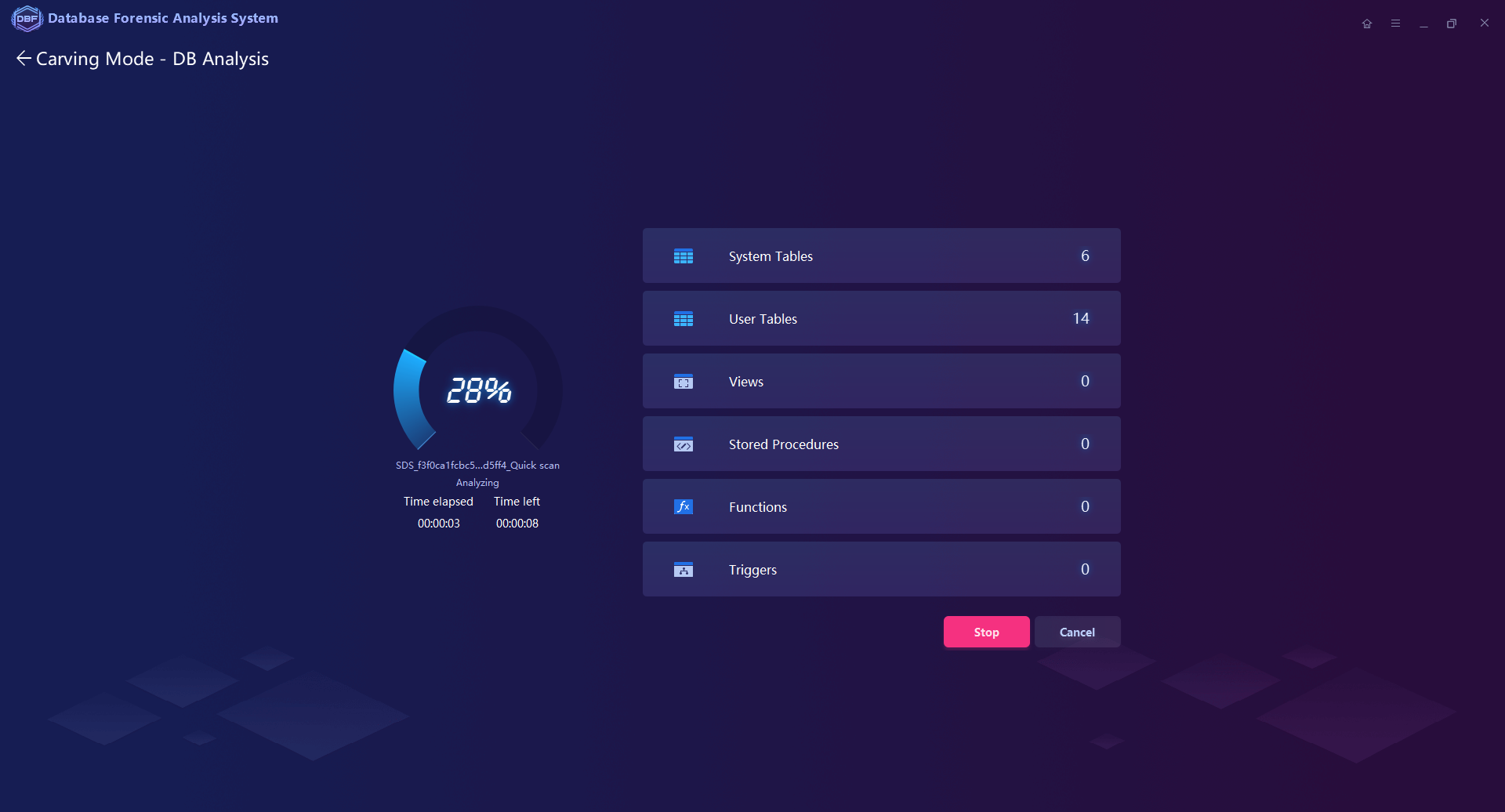
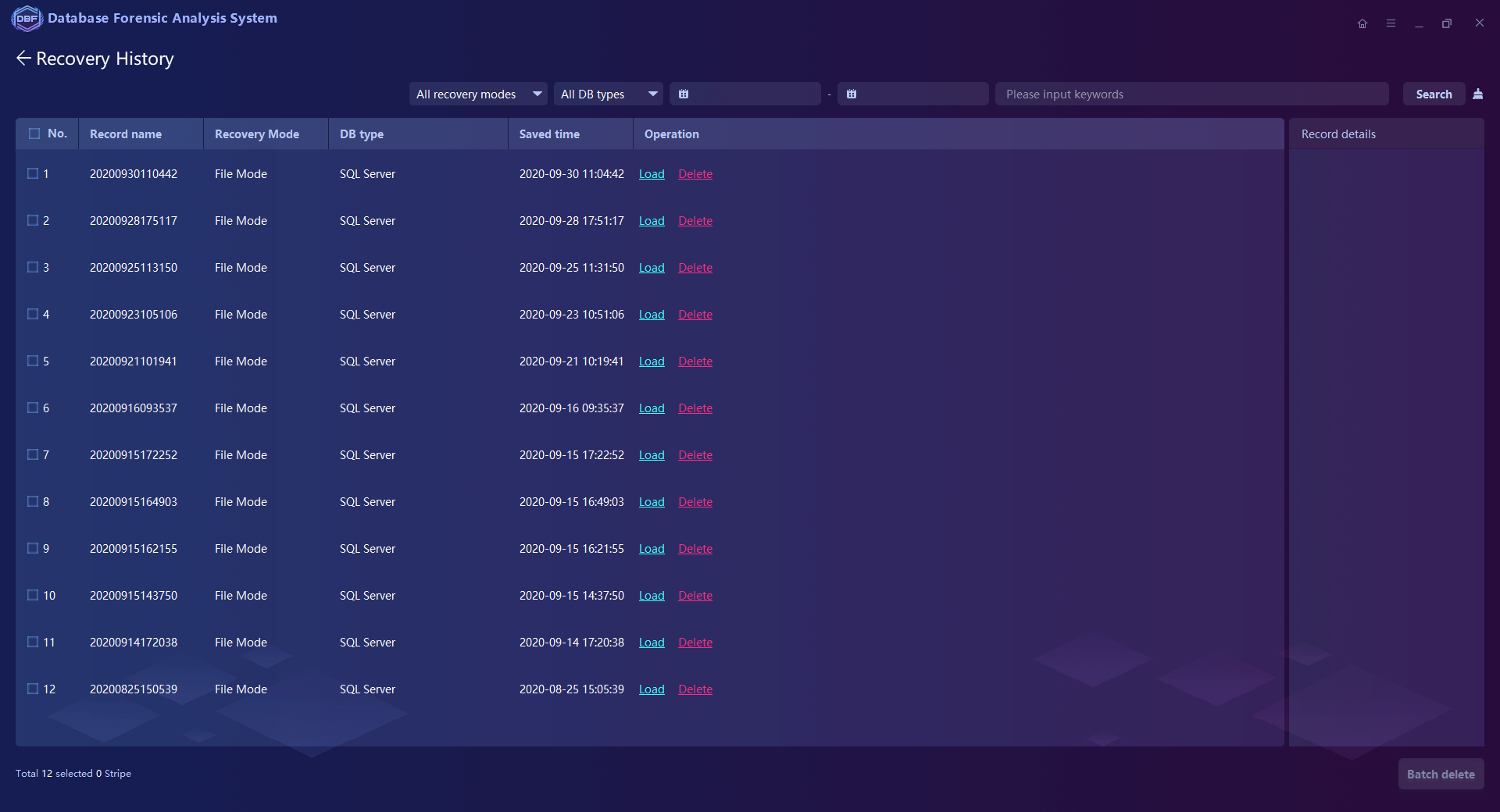
Extraction and Recovery for the normal/deleted/damaged database files, including the objects like tables, views, stored procedures, triggers, functions
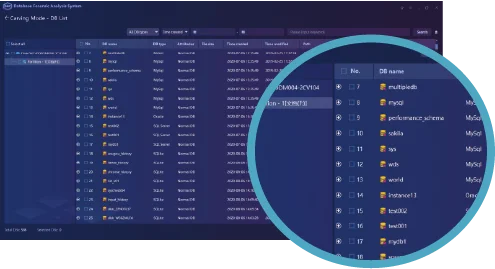
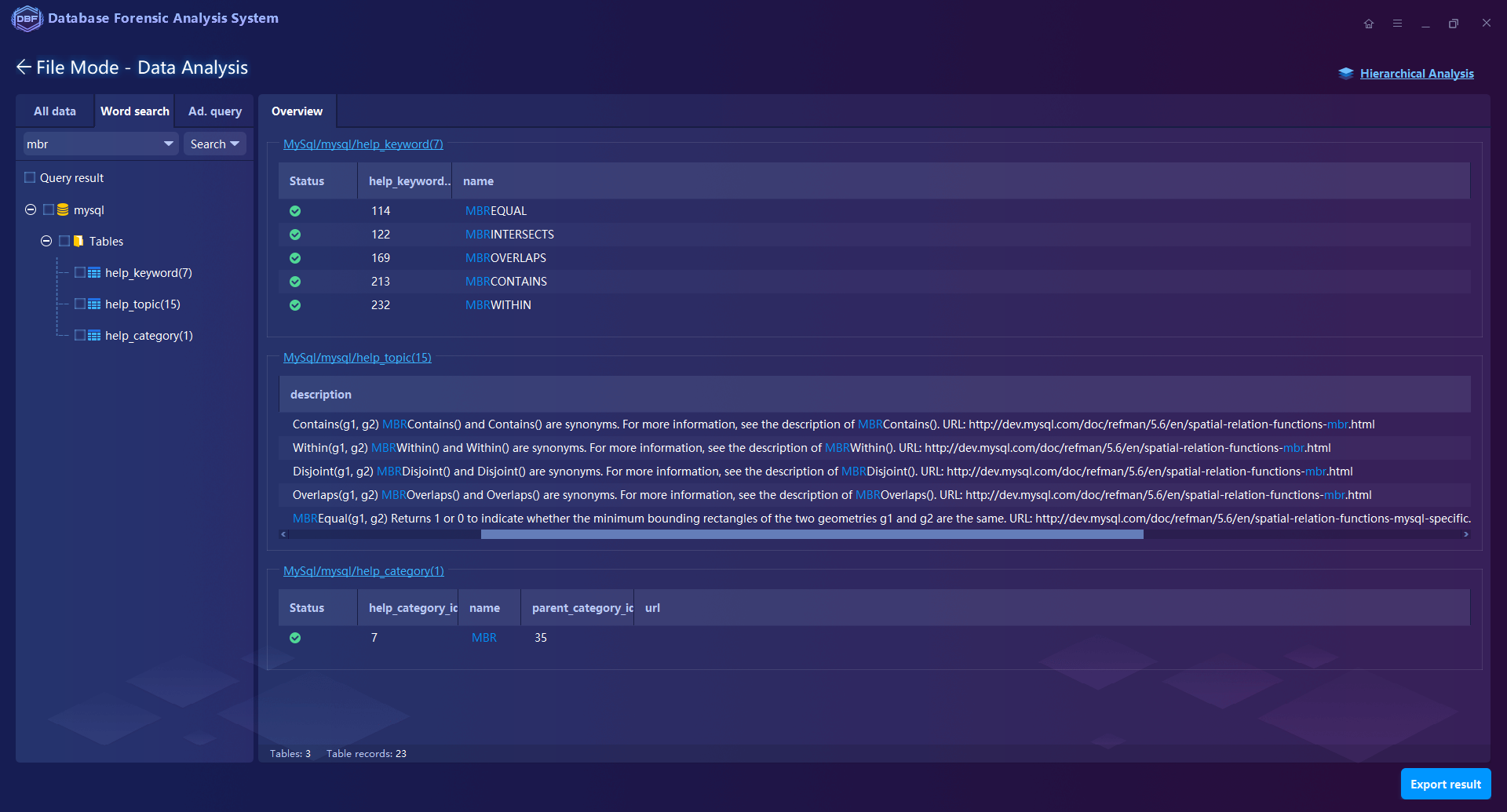
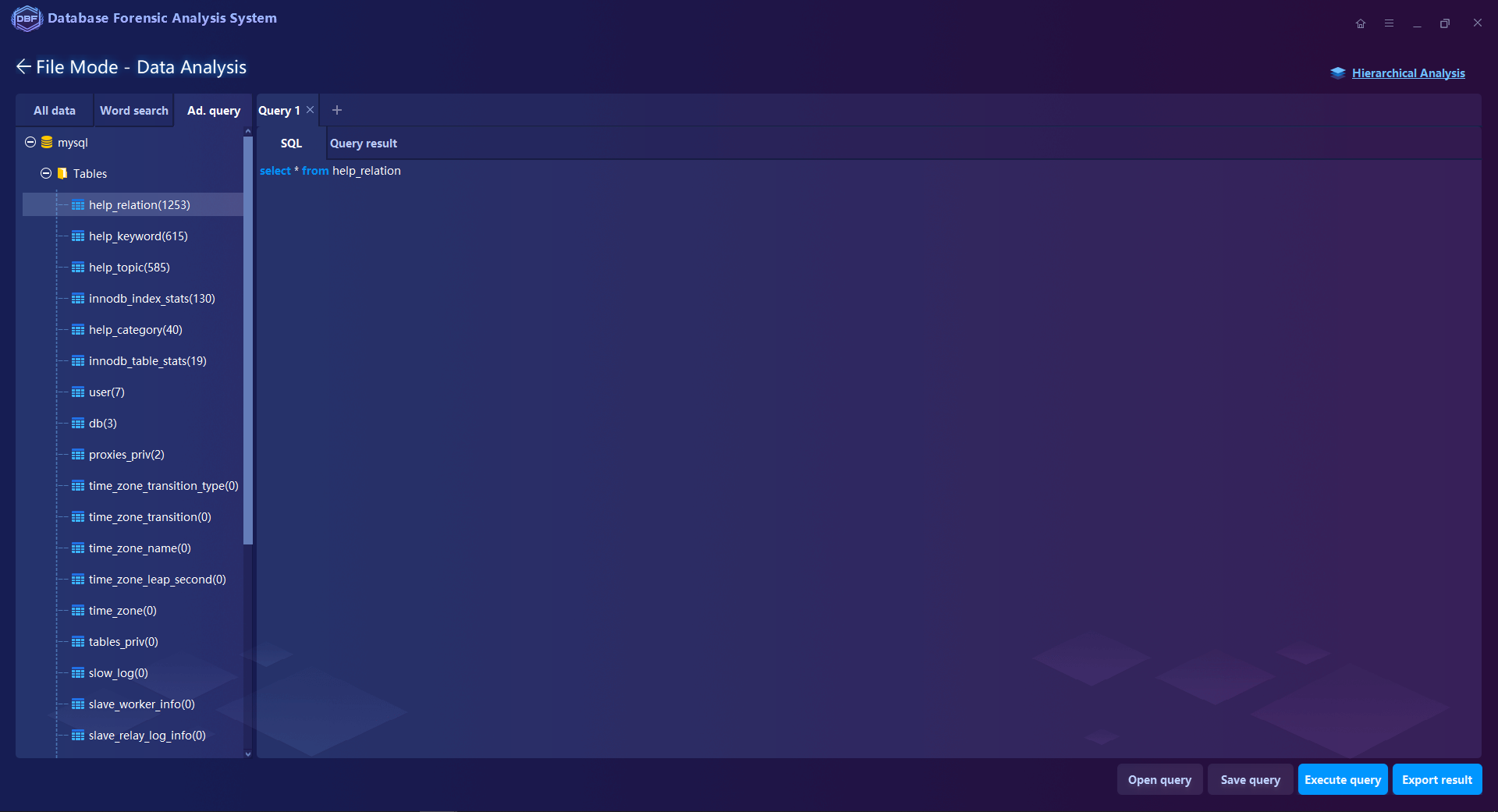
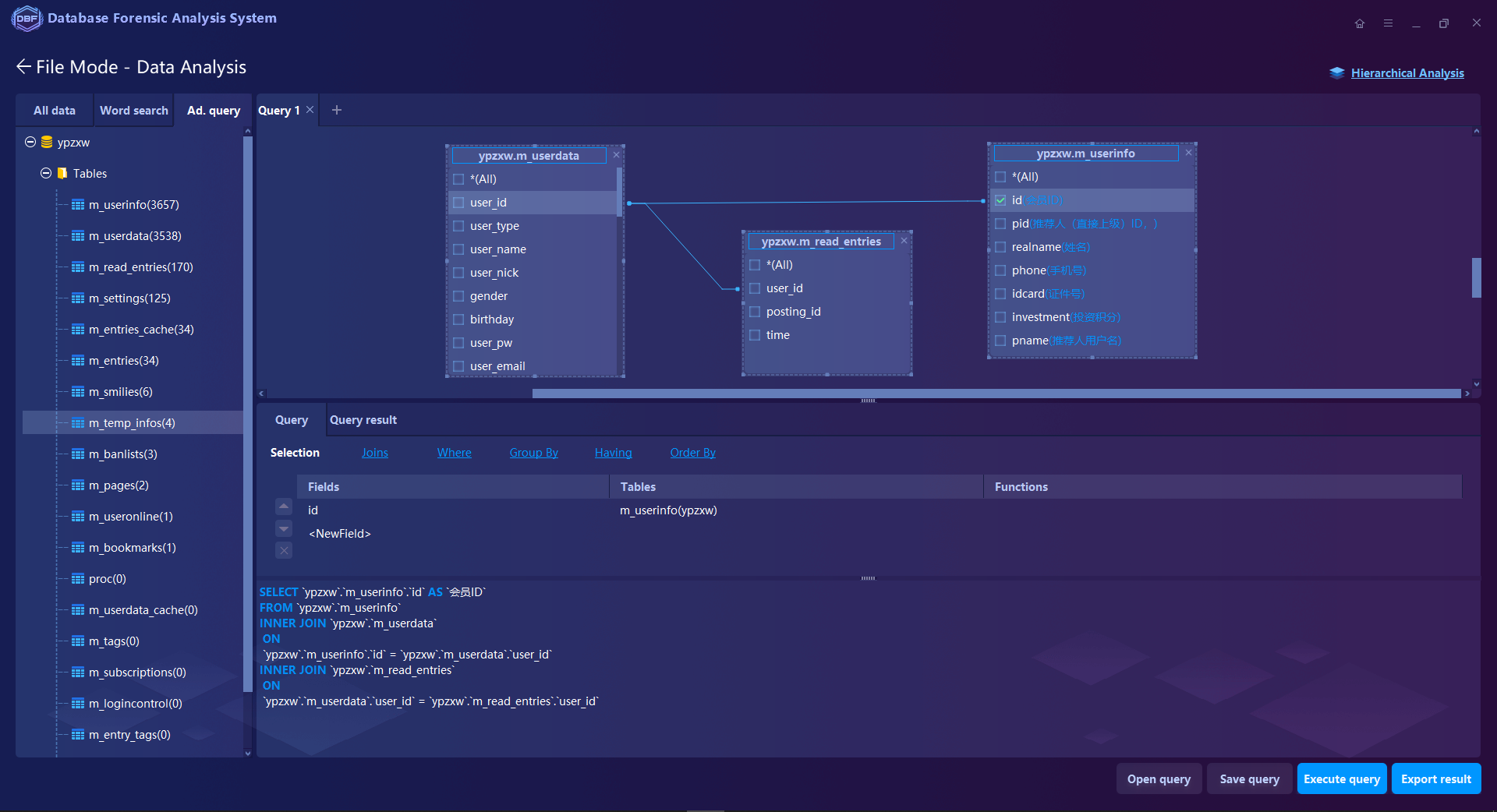
Multiple Analysis Functions such as keyword search, filtering, statistics, SQL statement query, and visual connection analysis. Supports to analyze the database log files of MySQL, SQL Server, Oracle, MongoDB, Elasticsearch, Hbase …
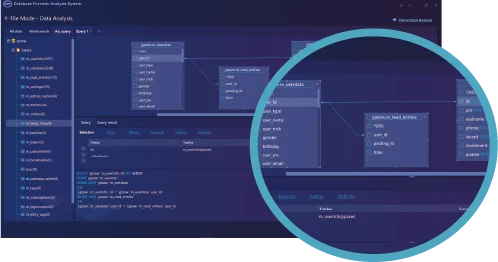
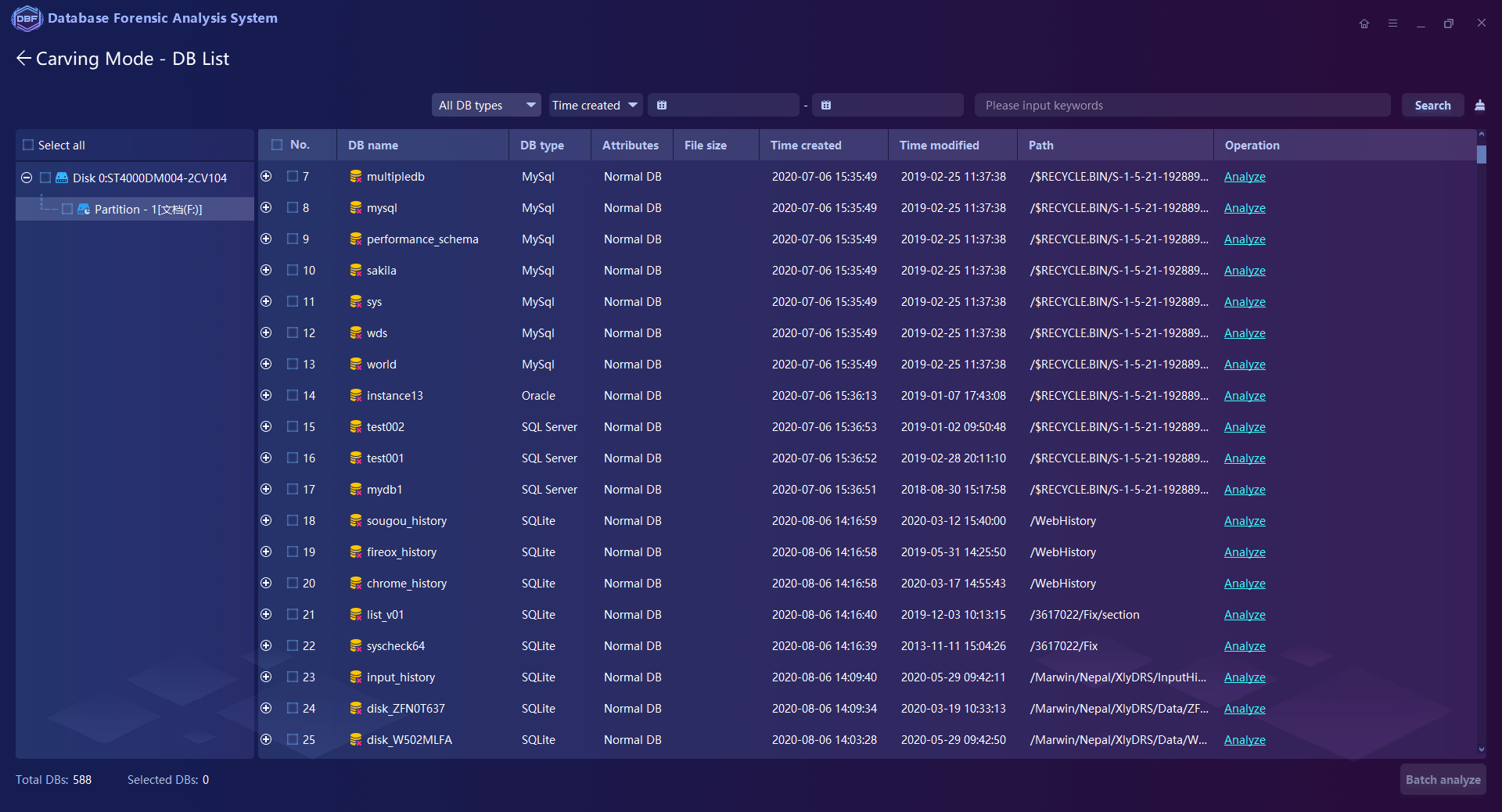
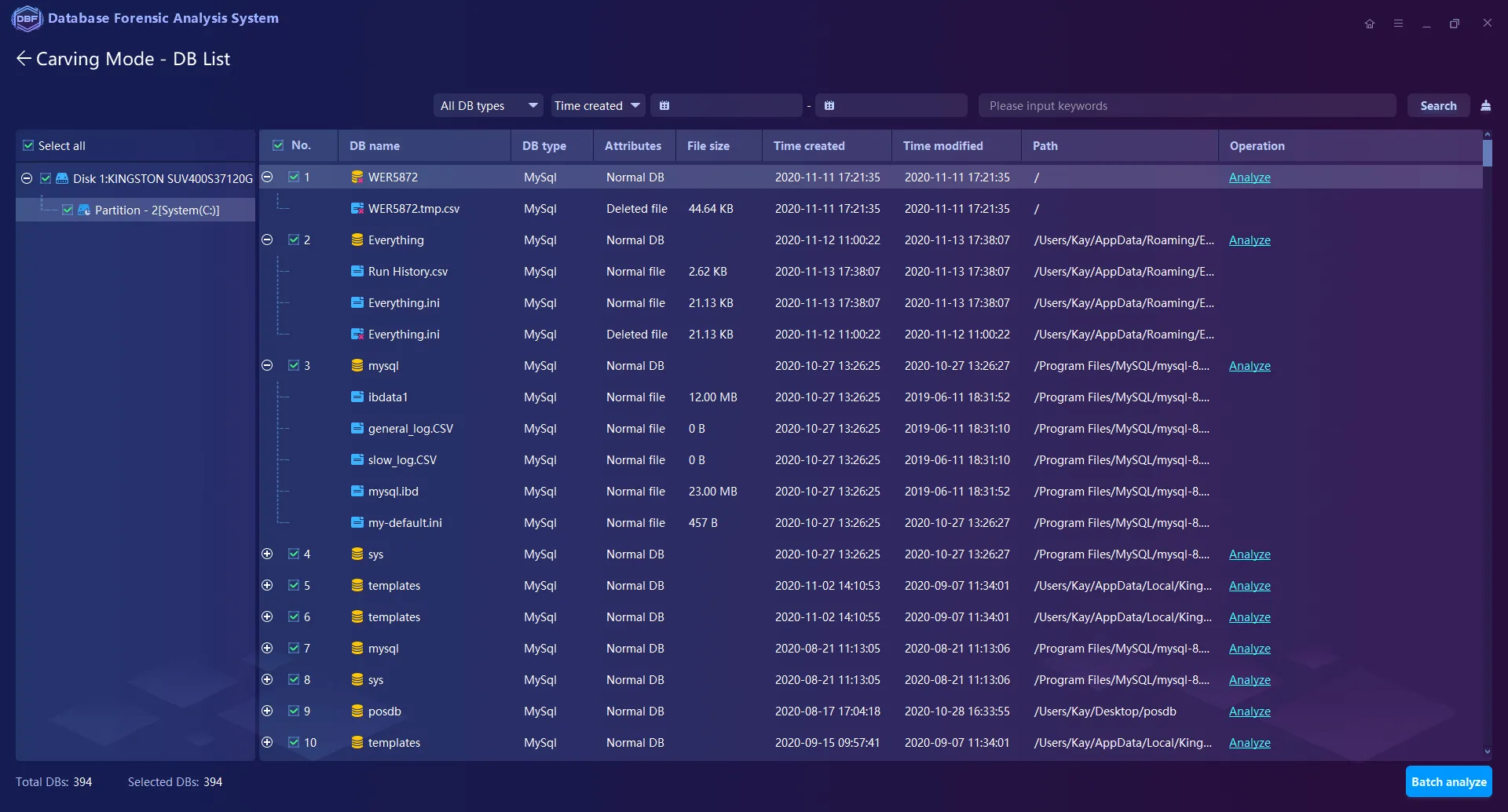
Patented File Carving Technology supports directly extracting, analyzing, and reorganizing the fragmented database files from the storage mediums or image files.
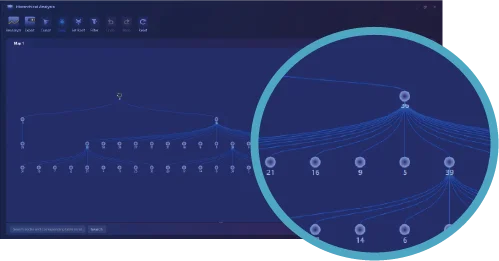
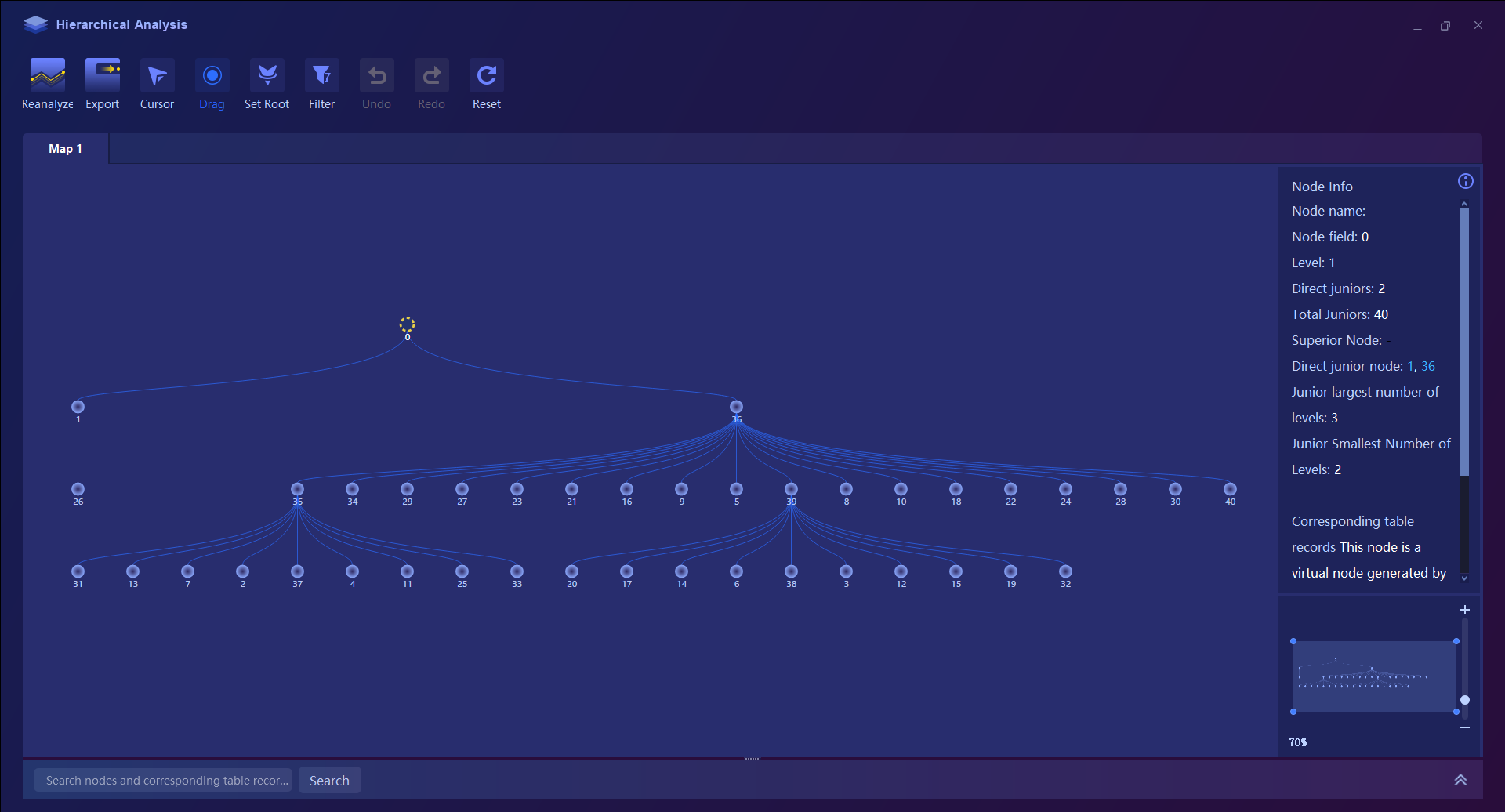
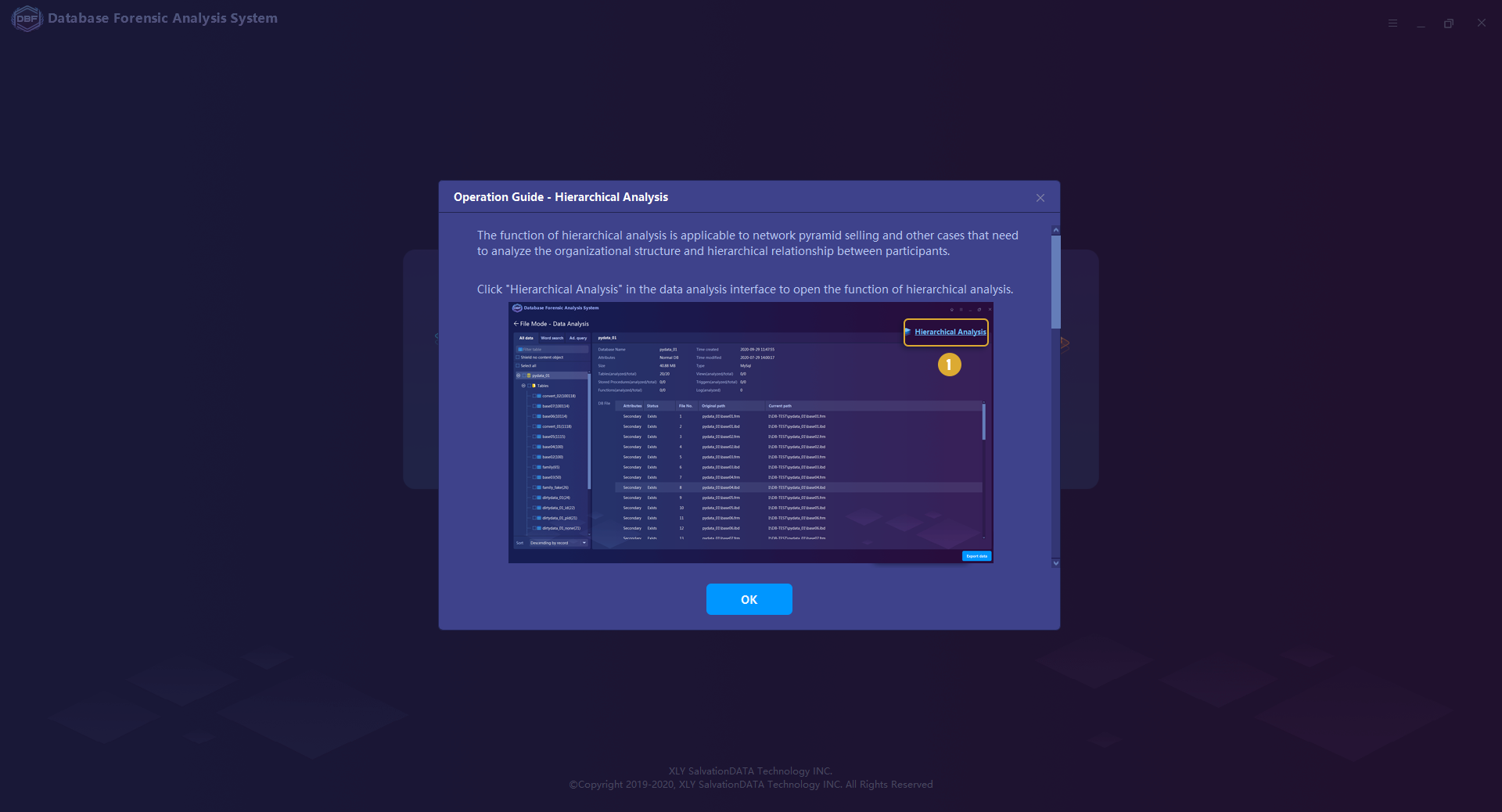
The hierarchical Relationship Analytical Tool supports generating and deriving hierarchical relationship maps.
Cloud Database Analytical and Conversion Tool supports the analysis of the MySQL database backup files (.xb) of Alibaba Cloud, Tencent Cloud, and Huawei Cloud, and export them to database files in conventional formats.
Forensic Reports Generation in HTML & PDF formats.
Exporting the Recovered or De-Duplicated Database Files.
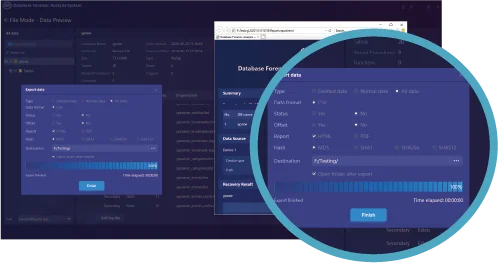
Software Operation Preview

One product, endless potential
What do customers say about our software?










Get deeper into the niche!
Discover how MD5 and SHA checksums guarantee file integrity. They create unique values to spot file corruption or tampering. Essential for data transfer, storage, and software checks.
Explore the AFA9500’s capabilities. From pre – checking devices to generating flexible reports, its automation features make mobile forensics a breeze.

SalvationDATA has new released the latest update of database forensics system V24.2.2411.2613.
Explore the top five database encryption techniques essential for securing business data and ensuring compliance with industry standards.


