What is Database Forensics?

-
Content
- What Is Database Forensics?
- History of Database Forensic
- The application of Database Forensics
- Who is a Database Forensic Expert?
- What is the Database Forensic Tool?
- Database Forensic Investigation Process
- Database Forensic Analysis System
- Summary
-
Content
- What Is Database Forensics?
- History of Database Forensic
- The application of Database Forensics
- Who is a Database Forensic Expert?
- What is the Database Forensic Tool?
- Database Forensic Investigation Process
- Database Forensic Analysis System
- Summary
What Is Database Forensics?
Database forensics is a subfield of digital forensic science concerned with the forensic examination of databases and their metadata. It is the use of electronic data stored in the database to reconstruct the clues, detect crime, and accomplish case cracking.
- The discipline is comparable to computer forensics, which follows the standard forensic method and employs investigative techniques on database contents and metadata. Additionally, cached data may exist in a server’s RAM, necessitating live analytic tools.
- Forensic analysis of a database may involve inspecting and validating the timestamps associated with the update time of a row in a relational table to validate a database user’s actions.
History of Database Forensic
If we look back upon the history of database forensics, it has got rid of the stale and brought forth the fresh during decades when more and more crime activities have been detected along with database development.
The 1970s
Financial fraud was a major target of cyber crime during this time period, which was common in this era for trained people with specific talents, such as those in banking, engineering, and academia to use mainframe computers for their work. When workers in these fields realized they could make money by altering computer data, they began engaging in white-collar crime. The one-half-cent crime was one of the most well-known crimes of the mainframe era.
It was difficult for law enforcement officers to ask the correct questions or preserve evidence for trial during this period since they were unfamiliar with computers at the time. Many began to attend the Federal Law Enforcement Training Center (FLETC) programs designed to train law enforcement in recovering and analyzing digital data, especially databases.
The mid-1990s
The rise of the database sector was sped up by the Internet’s arrival. The majority of desktop users used client-server database systems to access data on computer systems, which stored numerous information as time went by.
The late 1990s
FrontPage, Java Servelets, Dream Weaver, ColdFusion, Enterprise Beans, and Oracle Developer 2000 are some of the Internet database connectors that have seen an increase in demand due to the rising investment in online enterprises. Open-source platforms like Apache, MySQL, and CGI became popular among web developers as a result of their widespread use. When POS technology became more prevalent, online transaction processing and online analytics processing became more advanced. Meanwhile, corruption, money laundering, online financial fraud, and more related cases emerged, which forced law enforcement to learn and look deeply into relevant databases and utilize database forensics techniques accordingly to detect.
The 2000s
Database applications have grown despite the Internet’s collapse in the early 2000s. For PDAs, POS transactions, and the consolidation of vendors, new interactive programs were developed. Microsoft, IBM, and Oracle are currently the top three database vendors in the Western world.
It ended up with MySQL, SQLServer, and Oracle being the mainstream types of database systems.
At Present(2021 – )
Databases have become an integral part of our daily lives. Many of the services we take for granted now are only available because of databases, from personal cloud storage to weather forecasting. There is a slew of new non-relational database vendors popping up all the time. Oracle, MySQL, and DB2 are just a few of the contemporary relational database titans.
More importantly, more advanced technology has also been applied to the digital forensic field based on databases, which makes it utilized more widely in current society.
The application of Database Forensics
The database forensics technique has begun to apply widely among law-enforcements in recent years, which has also rapidly expanded its application scenarios.
A database forensic investigation may be focused on discovering transactions within a database system or application that suggest proof of illegal activity, such as FRAUD. (For some real application scenario use cases, you could check out this post for a better understanding.)
- To facilitate processing and data querying, the most prevalent types of databases in use today are often modeled in rows and columns in a sequence of tables. Thus, data may be accessed, managed, amended, updated, controlled, and organized with ease. The majority of databases write and query data using a structured query language (SQL).
- Database forensics examines who gets Database access and what actions are taken. Large-scale data security breaches are a significant issue, and criminal investigators look for pertinent information. Forensic analysis of a database may include an investigation of the timestamps indicating when a record in a relational table was updated.
However, In order to better implement the above techniques to effectively assist crime investigation, working with Database Forensic Experts / Database Forensic Investigators is always essential to most law enforcement.
Who is a Database Forensic Expert?
Database forensic experts are like detectives that investigate digital crimes. They hunt down cyberstalkers, cyberbullies, and sexual predators by identifying malevolent hackers, identity thieves, and online fraudsters.
The evidence they unearth may also be used to solve crimes in the “analog” world, such as murder, theft, white-collar robbery, etc.
Generally, Database Forensic Experts / Database Forensic Investigators responsibilities include:
- Investigating computer systems and other digital storage devices for evidence.
- Investigating with the use of forensic tools for disks and databases as well as file readers and network forensic software
- Using software to examine email, computer registries, and files as well as mobile devices
- Recovering vital documents and images that have been destroyed or encrypted.
- Writing and speaking about discoveries.
- Providing digital evidence to corporate authorities, law enforcement, and the courts.
- Detecting and remediating security breaches.
However, though database forensic expert / database forensic investigators has always been skillful and talented in dealing with digital forensic investigation especially when it comes to database forensics, supporting tools would never be a lack throughout all their career.
Working with scientific and trustworthy digital forensic tools in database forensics, not only make their workload burden decrease but makes the whole law-enforcement agencies possess advanced modern investigative techniques.
What is the Database Forensic Tool?
Investigations based on database forensics may be used for many purposes. One of the most usual ways to do this is in a court of law, whether in a criminal or civil context. Attributing evidence, verifying alibi or statement authenticity, ascertaining purpose, pinpointing origins, and verifying documents are all possible using database forensics.
In order to be fully qualified under the standard of being a piece of evidence according to the judicial principle, the digital evidence being as database files has to be retrieved and recovered completely and integrally.
In a way, working with database forensic tools is crucial to whatever investigation entities, no matter it’s digital forensic investigators, police officers, or special intelligence agencies when dealing with database evidence.
Luckily, there are several resources available to assist you in making this procedure quick and straightforward. These programs provide comprehensive reports that may be utilized in judicial proceedings.
The following is a hand-picked list of digital forensic toolkits, which are both open-source (free) and commercial (paid) software on the list.
DBR for MySQL is capable of restoring broken, damaged, or unavailable MySQL databases, including database tables, views, functions, stored procedures, and triggers. It can scan and retrieve deleted data from the Database in addition to restoring it.
DBR for SQLServer is a robust and efficient SQLServer database repair tool that can fix corrupted, damaged, or unavailable SQLServer databases, including database tables, views, functions, stored procedures, and triggers. Along with database restoration, it can also examine and retrieve lost data from the Database.
DBR for Oracle is a very effective and powerful Oracle database repair tool that may be used to restore corrupted, damaged, or unavailable Oracle databases, including database tables, views, functions, stored procedures, and triggers. Along with database restoration, it can also examine and retrieve lost data from the Database.
- ProDiscover Forensics
A tool for computer security, ProDiscover Forensic enables you to find all the data on a hard drive. For legal proceedings, it can protect evidence and provide high-quality reports. You can use this program to get JPEG’s EXIF data out of the image file format.
- Sleuth Kit (+ autopsy)
Sleuth Kit (+Autopsy) is a Windows-based utility package that simplifies forensic investigation on computer systems. This application enables you to inspect the contents of your hard disk and smartphone.
- FTK Imager
Developed by AccessData, FTK Imager is a forensics tool that may be used to obtain evidence. Without tampering with the original evidence, it can make copies of data. To limit the quantity of irrelevant data, this program enables you to choose file size and pixel size criteria.
- EnCase
Encase is a program that aids in the retrieval of data from hard drives via encryption. An in-depth investigation of files may be conducted to gather evidence such as documents and photos.
- System for Interfacing with Financial Transactions (SIFT)
SIFT Workstation is built on Ubuntu. In terms of digital forensics and incident response, it’s one of the most excellent computer forensic tools available.
- The FTK Imager software
To gather evidence, AccessData created the forensic tool known as FTK Imager. It is able to make copies of data without tampering with it. It is possible to reduce the quantity of data by specifying criteria such as file size, pixel size, and information type.
However, most of the above digital forensic tools are incapable of the overall procedure due to the below standard workflow of Database Forensic Investigation.
In such a case, we’re supposed to figure out what it specifically is to implement a rigorous and eligible database forensic investigation.
Database Forensic Investigation Process
- Acquisition & Recovery
To recover the deleted files and inaccessible files has always been the first step no matter it’s a database or other digital evidence in digital forensics. Without a scientific recovery process, no database files could be applied to any further steps, and let acquisition alone.
However, there are always deleted and damaged database files, especially when it comes to financial crime activities like online transaction fraud, money laundering, etc.
- Inspection
Access the targeted database files during the inspection step, so that it’s realizable to gather all needed files to proceed with analysis in the next step. However, obstacles often happen during the process since database files with passwords & accounts and related confidential requirements would prevent unauthorized users from accessing, which has been occurred in numerous cases we know so far.
- Analysis
Overall analysis for all available/normal database files retrieved from the database is the vital process in which potential case cracking direction could be as a result, only if it’s trustworthy enough along with potential clues.
Thus, the analysis method takes up the major factors in generating a reliable result.
- Reporting
After giving all reliable analyses on the available database files, it’s time for formulating a referential Digital Forensic Report. At this point, a visual and hierarchical map to point out suggestions and tactics would be the best reference and methodology for deeper investigations.
In fact, as we already know simple supporting tools sometimes do not work effectively and scientifically, the database evidence could be ended up not being admissible in court, even after tons of workload on dealing with the problematic files in certain cases.
Thus, learning about DBF(Database Forensic System) from SalvationDATA today could be an advisable option to scientifically conduct database forensics and avoid not admissible evidence from being occurred.
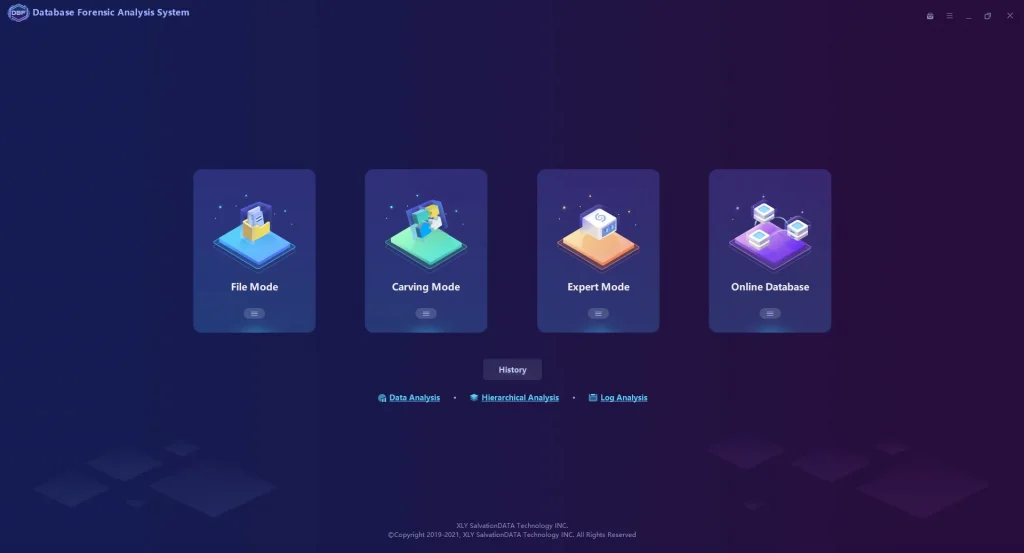
Database Forensic Analysis System
So far, there is no integrated Database Forensic Analysis System all over the world to cover all processes in Database Forensics including Acquisition & Recovery, Inspection, Analysis, Reporting, except DBF from SalvationDATA.
Contact to apply for a Free Trial now!
DBF series covers forensic database systems for both relational and non-relational databases, as the world’s premier database forensic supporting system.
In order to resolve the above-mentioned obstacles during each step, it has been put into well-researched and development for corresponding capacities just to fulfill both the case cracking demand and being admissible in court.
Meanwhile, without the need for a pricey expert or a complex set-up environment is going to help law enforcement or demand entities implement such effective and most available supporting tools with less hesitation.
- Acquisition & Recovery
Designed to overcome the obstacles in database files acquisition & recovery, deleted/corrupted/fragmented databases, false file systems, and application system access restrictions, most of the potential problems have been addressed by DBF, even data inside inaccessible tablespaces or tables, views, stored procedures, triggers, functions, etc.
- Inspection
When encountering required confidential information, it’s now been resolved by the patented technology from SalvationDATA to bypass. Consequently, it makes most of the database files have been able to be accessed without restriction and initial configuration of the database environment possible.
- Analysis
-
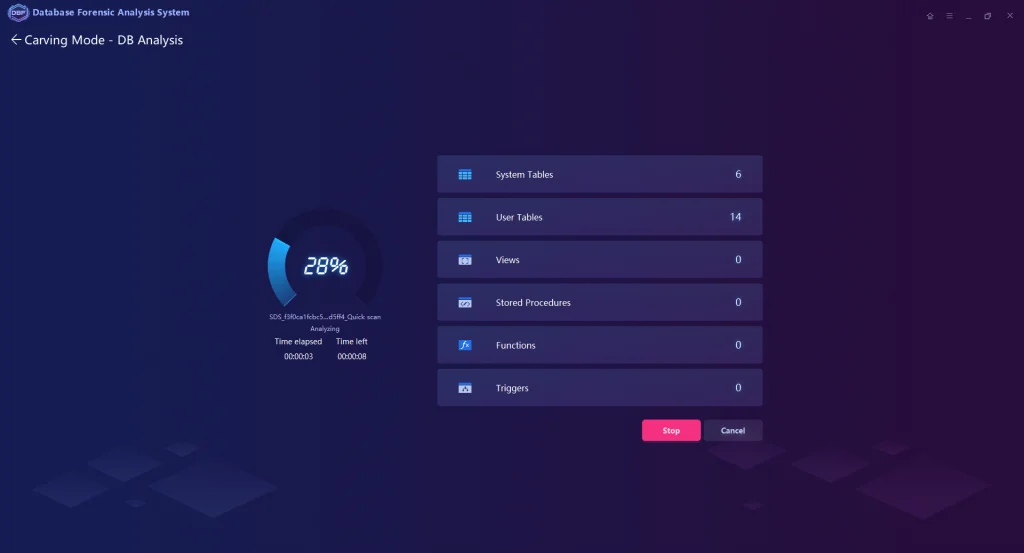
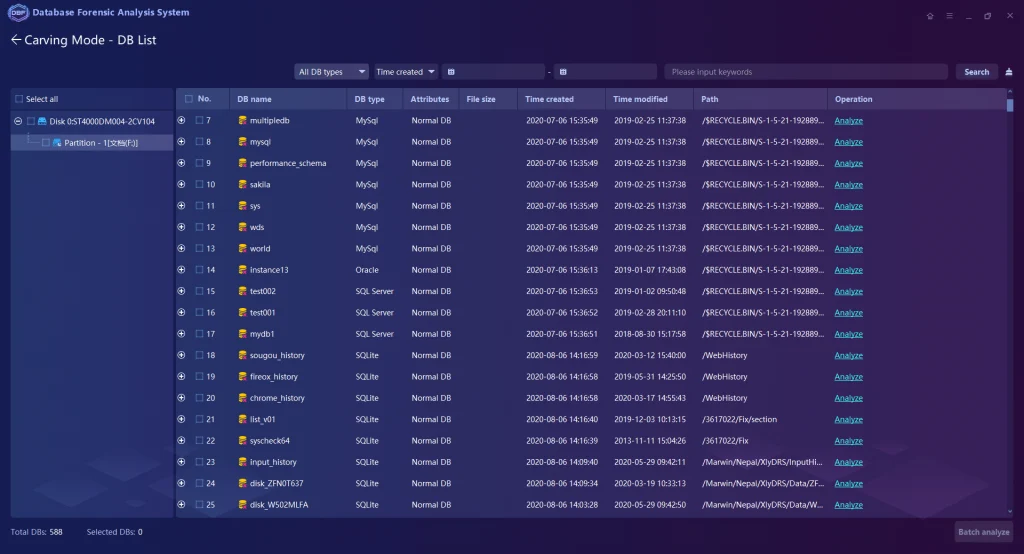
- File Carving Technology from DBF is capable of extracting, analyzing, and rearranging fragmented database files directly from storage mediums or image files
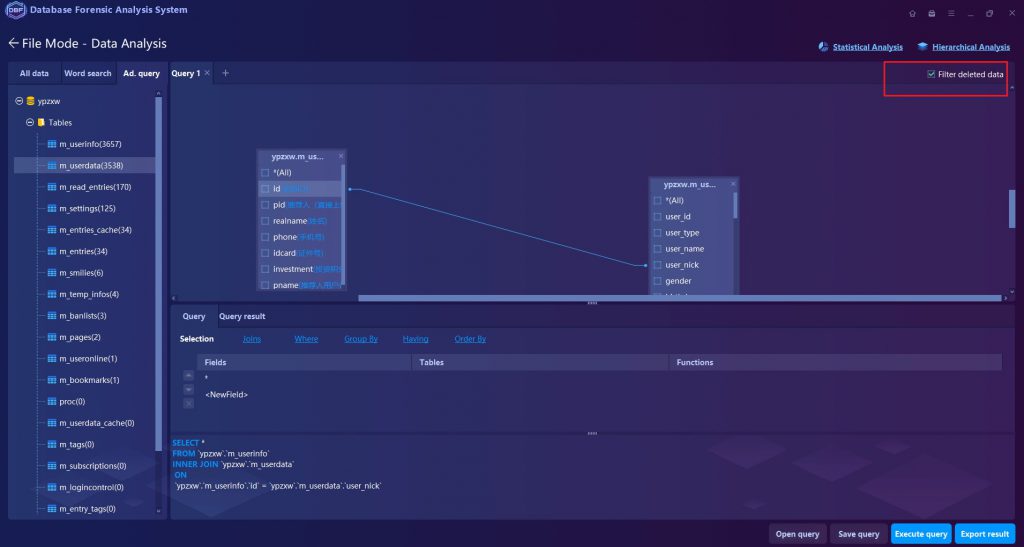
- Multiple Analysis Functions such as keyword search, filtering, statistics, SQL statement query, and visual connection analysis have been implemented completely in DBF. Besides, it supports the analysis of the database log files based on both relational databases MySQL, SQL Server, Oracle, and non-relational databases.
- Reporting
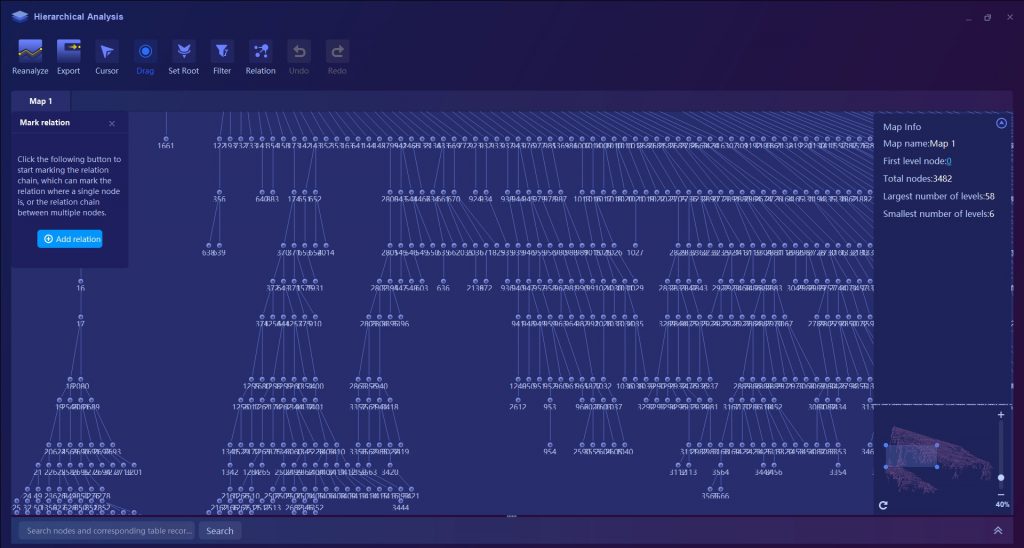
With its Hierarchical Relationship Analytical Tool to create and interpret the hierarchical relationship maps, the investigators are capable of receiving the most visualized and analyzed analysis report. So that, other departments, especially courts could consider them more admissible!
Summary
Database Forensics is never a common investigation work when compared to other digital forensic works like video forensics, mobile forensics, etc, even if it’s conducted by database forensics experts / database forensics investigators. Without deep knowledge reserved in database-related technology, it would be frustrating and end up with no admissible evidence in court probably, unless scientific supporting tools or database forensics systems are out there to assist.
In recent years during the development of databases, database forensics has begun applied widely among countries in their law enforcement, military, and intelligence.
After today’s article, we’re assuming you know better about database forensics and how should you take care of it!