How to Extract Data From Android Emulator NoxPlayer?
Overview
The android emulator can simulate the android operating system on the computer, and can install, use, and uninstall tool software for android applications. It allows users to experience the whole process of operating the android system on the computer.Because of its simple operation and low cost, it is often used by criminals to carry out illegal and criminal activities.For the data of Facebook, Whats app and other applications in the android emulator, if the technicians do not understand the relevant criminal techniques during the evidence collection process, it will cause the missing of application data running on the android emulator. Therefore, we need to understand the data situation of Android simulation and master its evidence collection methods. At present, relatively common android emulators include “NoxPlayer”,“LDPlayer”, and “MEmu”.
How to Extract Data from Android Emulators Successfully?
Here are ideas and steps:
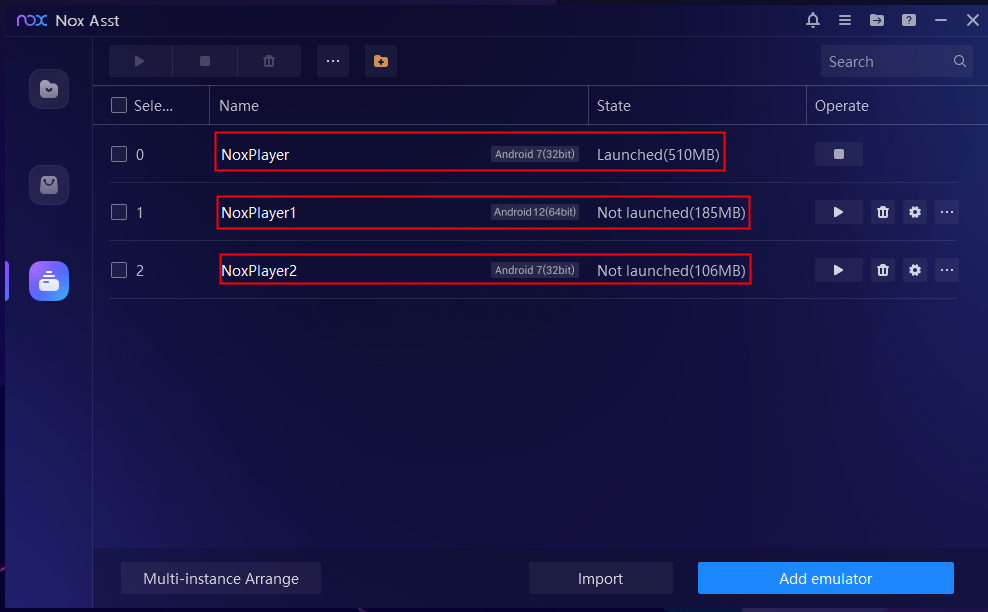
1.Find and confirm the android emulators
First of all, pay attention to possible situations:
- Multiple android emulators are opened simultaneously.
- Android emulator software is uninstalled or data is deleted.
- There are multiple android emulators installed or the android emulator is installed on the VMware virtual machine.
2.Extract or recovery the data of android emulator
① General extraction key points of LDPlayer & NoxPlayer &MEmu
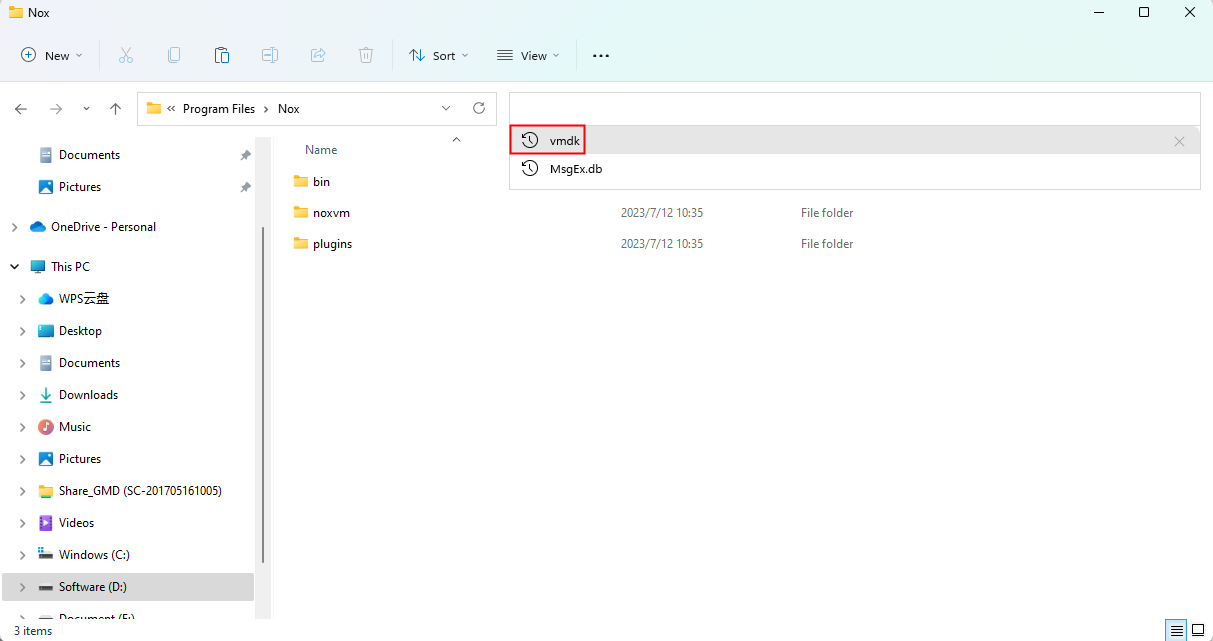
Find the corresponding virtual disk file in the format of vmdk in the image(the data of the emulator uses a virtual disk file for storage), it may also be a virtual disk file in other formats, such as: vdi .
The method of finding file in the format of vmdk: Directly search for ” vmdk ” in the emulator installation directory, the above method is also applicable to files in other formats.
The storage path of the file in the format of vmdk for NoxPlayer :
D : \ Program Files \ NoxPlayer \ bin \ BignoxVMS \ Nox
The storage path of the file in the format of vmdk for LDPlayer :
D : \ Program Files \ LeiDian \ LDPlayer 4.0 \ vms \ LeiDian
The storage path of the file in the format of vmdk for MEmu:
D : \ Program Files \ Microvirt \ MEmu \ image \71
The storage path of the file in the format of vmdk for MEMu:
D : \ Program Files \ MEmu \ emulator \ MEmu \ vms \ MEmu -6.0- x64 – default
- Multiple android emulators are opened simultaneously:
Please find relevant information in the settings of the emulator to confirm, and then to extract.
- Android emulator software is uninstalled or the data is deleted:
Method 1-When the android emulator NoxPlayer is uninstalled or the data is deleted, please recover the data of the emulator’s virtual disk file. Normally, the scan path for recovering data is the same as the path for storing virtual disk files, the storage path may also be different according to the actual situation (the data level of this type of virtual disk is similar to partitioning in the partition,which means the Sub- partition space and the underlying data is not encrypted);
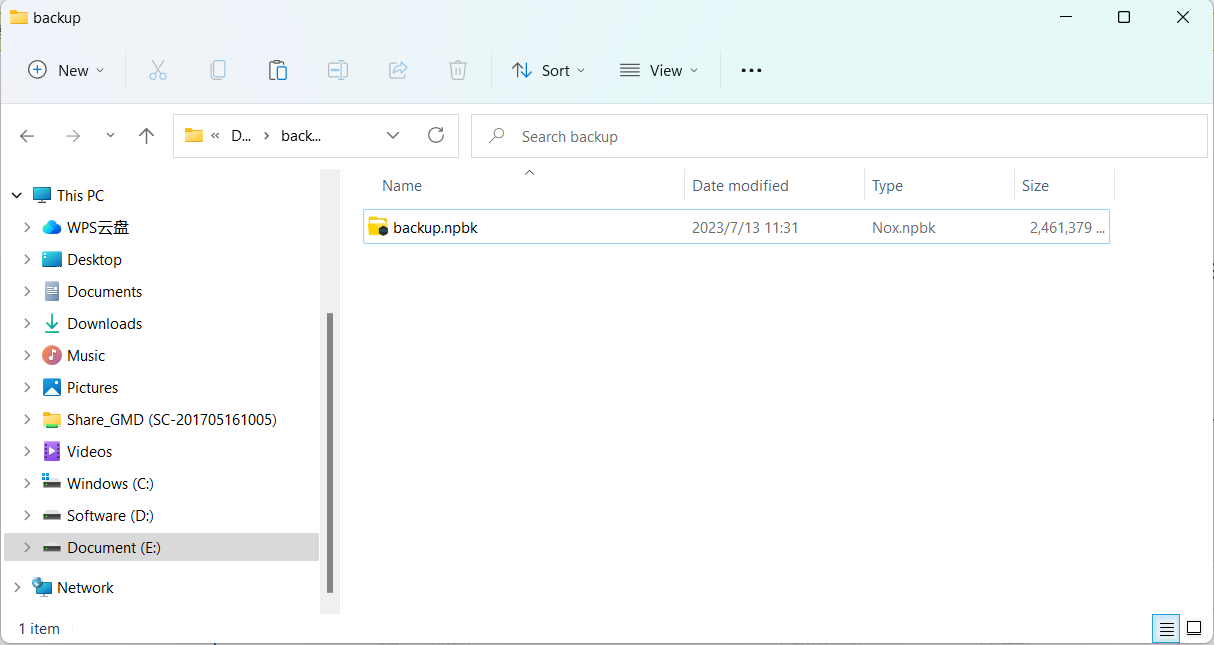
Method 2-Try to find the backup file of the emulator, Firstly restore the backup file and then carry out the extraction process. the android emulator can be backed up through its built-in backup tool. After the backup is complete, an image file with the extension “.xxx” will be obtained. (NoxPlayer is “.nupk “; LDPlayer is ” .ldbk ” ; MEmu is ” .ova “).
- There are multiple android emulators or android emulators installed in VMware Virtual Machine.Just do more searches , and then extract relevant data after locating the android emulator.
③Use mobile forensic tools to Analyze Data
Load the found virtual machine vmdk disk file of the android emulator into the mobile phone forensics tool for analysis to get the relevant data. Some emulators need to manually find the involved files from the vmdk disk file to be parsed.Only in this way, the relevant data can be obtained.
Case Study
Take the backup file of the “NoxPlayer” as an example to extract data .
- Tools:NoxPlayer 0.1.3, SPF Pro Smartphone Forensics System Professional
- Inspection material: npbk
Operation steps:
Step1.Install the new version of “NoxPlayer”
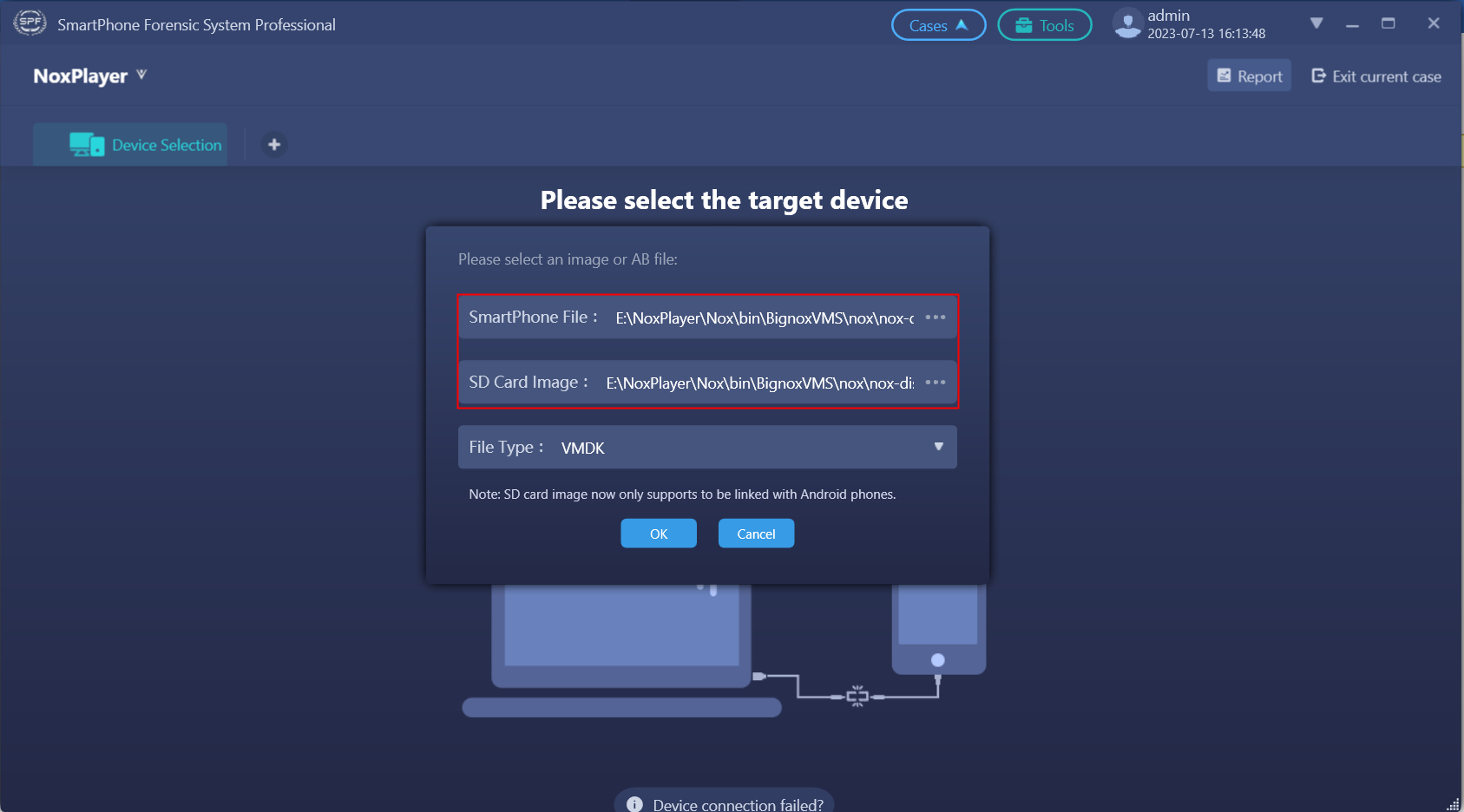
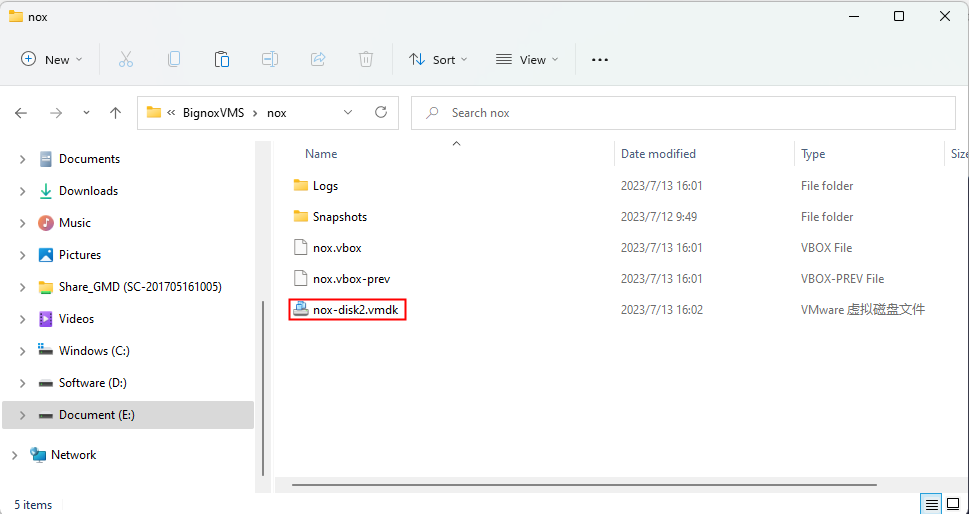
Restore the android emulator , and find the data image of the emulator in the format of vmdk by file search function.
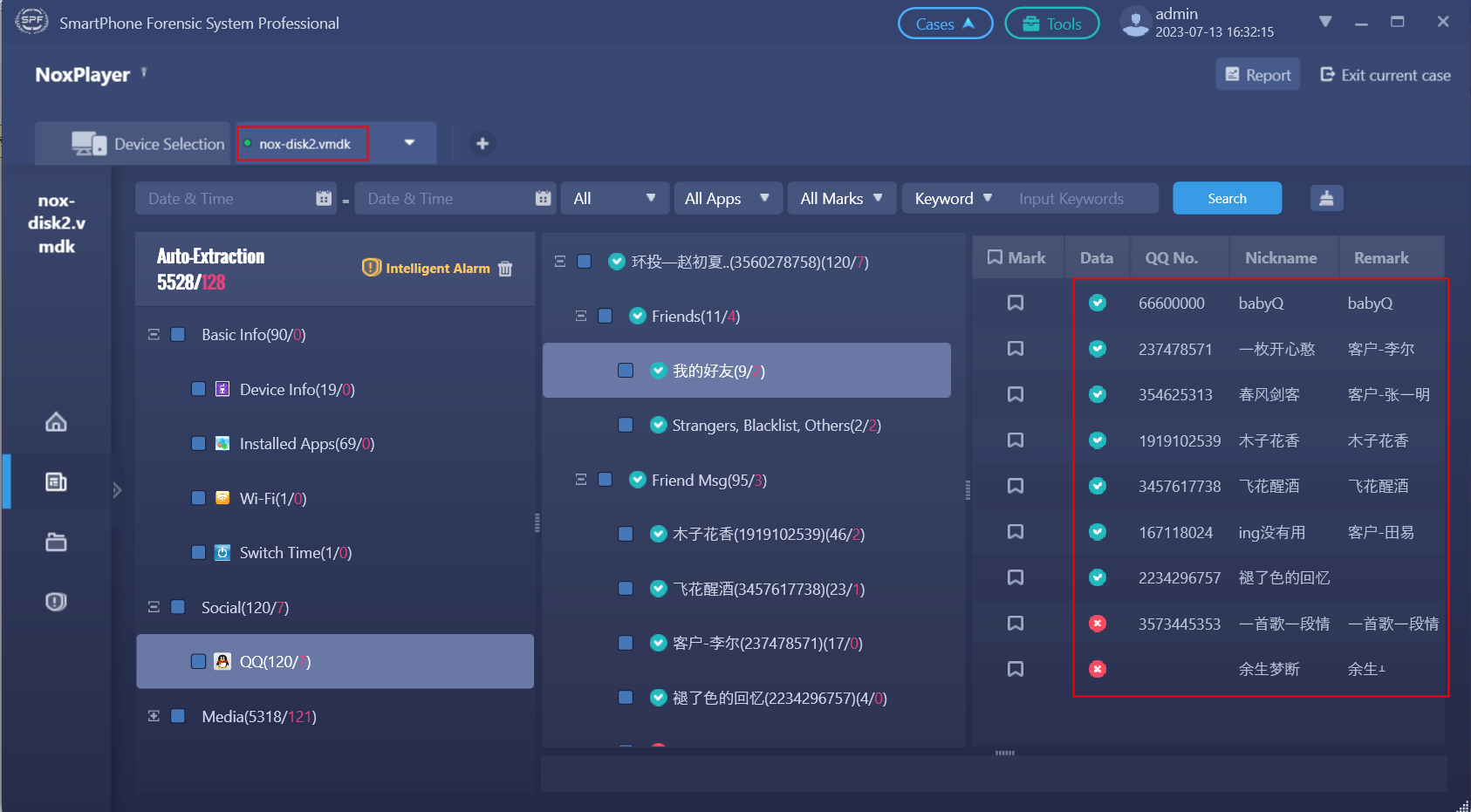
- Load the virtual disk file into the SPF Pro Smartphone Forensics System to analyze.
- Select the “Automatic Logical Extraction” to complete the extraction. As shown in the figure below, both basic information and social media can be extracted, including some deleted data.
Cautions
- If the relevant android emulator NoxPlayer is not found on the computer involved in the case, please check the running traces of software, the software installation packages, the browser history, etc.
- After the APPs in the android emulator has been uninstalled, there is a greater probability of recovery than mobile devices.Please choose the correct data recovery method.