What are the 4 Common Types of Digital Forensics in 2024?

-
Content
- Introduction
- Overview of 4 Types of Digital Forensics
- Key Considerations in Digital Forensics
- Data Acquisition and Preservation
- Analysis and Interpretation of Digital Evidence
- Conclusion
-
Content
- Introduction
- Overview of 4 Types of Digital Forensics
- Key Considerations in Digital Forensics
- Data Acquisition and Preservation
- Analysis and Interpretation of Digital Evidence
- Conclusion
Introduction
Digital forensics mainly focuses on recovery and investigation of material found in digital devices, in relation to criminal & private investigations and cybercrimes. Various types of digital forensics have become a vital aspect of law enforcement agencies and businesses these days. It focuses on identification, preservation, examination, and analysis of evidence, using advanced tools and techniques. Digital forensics is used for the following purposes:
- In criminal cases, it involves the investigation of any illegal activity by cybercriminals. The cases are usually carried out by law enforcement agencies and digital forensic examiners.
- When the focus is more on protecting rights and property of individuals or settling contractual disputes between commercial parties, it comes under the purview of civil cases.
- Experts in this area of forensics are also hired by the private sector in their cybersecurity teams, in order to detect data breaches, leaks, and other forms of cyber threats.
The collected evidence could be used as part of intelligence gathering or to locate, identify or prevent other crimes. In this article, you will learn about the types of digital forensics tools, and how they can be useful.
Overview of 4 Types of Digital Forensics
1. Computer Forensics
Computer forensics, also known as cyber or digital forensics, is a branch of digital forensic science that involves the identification, collection, preservation, and analysis of electronic evidence from computer systems and digital devices. It plays a vital role in various scenarios, including criminal investigations, cybersecurity incidents, intellectual property theft, fraud cases, and employee misconduct.
Techniques and tools:
- Reverse steganography – evidence is discovered after analyzing the data hashing of the digital file in question. The underlying hash or string of data that represents the image will change, if it is tampered with.
- Disk Imaging: This technique involves creating a bit-for-bit copy or image of a storage device, such as a hard drive or solid-state drive (SSD). It ensures the preservation of the original data while allowing investigators to work on the copy to prevent any modifications or tampering with the evidence.
- File Carving: File carving techniques are used to recover deleted or fragmented files from storage media. It involves searching for file signatures or specific patterns of data to extract files that may have been intentionally or accidentally deleted.
- Cross-drive Analysis – correlation and cross-referencing of data on several computer drives to search for, analyze, and preserve information, as relevant to an investigation.
Applications:
Applications of computer forensics include collection of evidence, forensics tools and tasking, solving old cases, and usage in criminal investigations.
2. Video Forensics
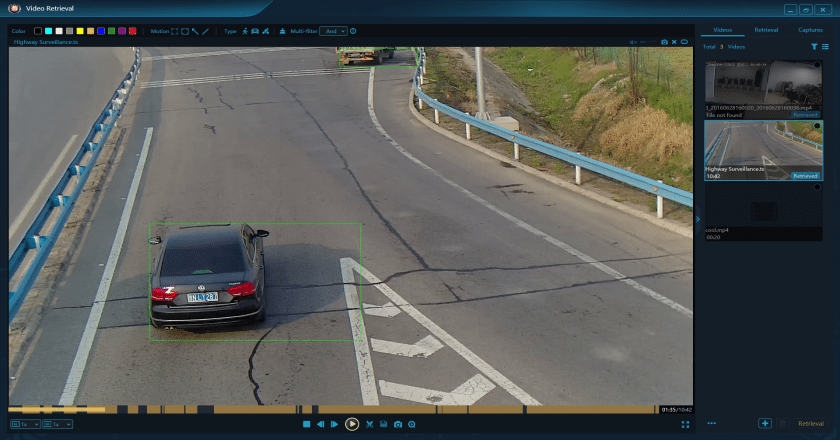
Video forensics refers to one of the digital forensics services and specialized tools to analyze and authenticate digital video evidence for investigative and legal purposes. It involves the examination and enhancement of video footage to extract valuable information, establish the integrity of the video, and provide evidence in legal proceedings. Video forensics aims to determine the authenticity, origin, integrity, and context of a video recording, ensuring that the video can be considered reliable and admissible in court.
Techniques and tools:
- Video Authentication: The process of verifying the integrity and authenticity of a video recording by examining its metadata, identifying signs of tampering, and detecting any alterations or manipulations that might have occurred.
- Video Analysis: Analyzing video content to extract valuable information, such as facial recognition, object identification, motion tracking, and scene reconstruction, which can aid in identifying individuals, understanding events, or reconstructing crime scenes. Tools like VIP 2.0 is used widely in video forensics.
- Video Recovery: Recovering and restoring video data from damaged or corrupted sources, including video files that have been deleted, partially overwritten, or stored in fragmented or incomplete formats.
Applications and challenges:
Video forensics plays a crucial role in legal investigations, law enforcement, incident reconstruction, and security and surveillance by providing authenticated video evidence that can be presented in court. It helps verify the integrity of video recordings and aids in identifying individuals, events, or objects captured in the footage.
Video compression techniques, different file formats, and transcoding can introduce artifacts and affect the accuracy of video analysis. Analyzing video evidence that have undergone multiple encoding or transcoding processes can be complex.
3. Mobile Forensics
This type of digital forensics involves the recovery of digital evidence from gadgets that have internal memory and communication abilities such as smartphones, tablets, GPS devices, etc. These mobile devices store a wide range of information such as phone records and text messages, as well as online search history and location data.
Techniques and tools:
- Data Acquisition: Similar to computer forensics, data acquisition plays a crucial role in mobile forensics. Forensic experts use tools and techniques to acquire a forensic image or extract specific data from mobile devices. This can include extracting data from the device’s storage, SIM card, or cloud services. Tools like SPF Pro, Oxygen Forensic Detective, and XRY are commonly used for data acquisition in mobile forensics.
- Physical and Logical Analysis – it requires connecting the data cable to the device and recovering data using extraction software. Tools like MOBILedit, and Andriller facilitate physical and logical analysis of mobile devices.
- App Data Analysis: Mobile applications store a wealth of data on devices, including chat conversations, media files, location information, and user preferences. Forensic investigators employ techniques to extract and analyze app data to gather evidence. Tools like SQLite Forensic Explorer,Smartphone Forensics Pro, and XRY offer capabilities for analyzing app data from various mobile platforms.
Examples:
These types of digital forensics are used by the military to collect intelligence while planning operations or thwarting terrorist attacks. Corporations often use mobile evidence to prevent theft of intellectual property or catch an employee in the act of committing fraud. Law enforcement uses electronic discovery in cases like identity theft and homicide.
4. Database Forensics
This type of digital forensics is related to databases, including their metadata. The cached information may also exist in a server’s RAM requiring live analysis techniques. When databases are examined forensically, it could relate timestamps that apply to the update time of a row, in a relational database that is being inspected and tested for validity to verify the actions of a database user. It could be used to detect transactions within a database or application that indicates evidence of wrongdoing.
Challenges and considerations:
- Accessing logs – system administrators, developers, and forensic investigators require different logs for varied purposes.
- Volatility of data – data stored in a virtual machine (VM) instance in a cloud is lost if the VM is turned off.
- Multi-tenancy – multiple VMs share the same physical structure, but the investigator has to show logs by proving the malicious activities occurring from the different service providers.
Techniques and tools:
There are numerous database systems to choose from, but the most popular ones are listed below:
- Database Analysis Tools: Various tools are available to assist in the analysis of databases during forensic investigations. These tools provide features for examining the structure and contents of databases, extracting data, and analyzing metadata. Examples of such tools include DBF6300 , Oxygen Forensic Detective, and Forensic Toolkit for Databases (FTK Database).
- SQL Query Analysis: In database forensics, SQL queries play a significant role in interacting with and retrieving data from databases. Analyzing SQL queries can help identify suspicious or malicious activities, unauthorized data access, and data manipulation. Tools like MySQL Enterprise Audit, PostgreSQL log analyzer, and Microsoft SQL Server Profiler assist in analyzing SQL queries.
Key Considerations in Digital Forensics
1. Legal and Ethical Considerations
-
Importance of adhering to legal and ethical standards
Types of digital forensics deal with discovering and preserving evidence that can be used in court. Those who are involved in this field need to have a solid understanding of the laws and regulations that pertain to data protection. Professionals must avoid the criminal charges or civil penalties that can result from the mishandling of digital evidence.
-
Laws and regulations related to digital forensics
Legal considerations that come into play in digital forensics, such as an individual’s right to privacy. Forensic investigators have to be careful that there are no violations of laws such as the Wiretap Act and the Stored Wired and Electronic Communication Act, as it could lead to federal felonies.
2. Ethical responsibilities of digital forensics practitioners
While investigating a case, digital forensic practitioners can come across sensitive data, without getting a proper warrant, which violates the individual’s right to privacy. There is also potential for bias and discrimination, while collecting and analyzing evidence. Therefore, all professionals involved in various types of digital forensics, have to receive ongoing training on ethical practices, while staying updated regarding privacy laws and regulations.
Data Acquisition and Preservation
1. Methods for acquiring and preserving digital evidence
Gathering and recovering of sensitive data using different types of digital forensics, is known as acquisition. Investigators should know how to access, recover, and restore the data, and protect it for future management. Commonly used data acquisition methods include:
- Bit-stream disk-to-image files – a disk drive is cloned, so all necessary evidence is preserved.
- Bit-stream disk-to-disk files – tools are used to create a disk-to-disk copy
- Logical acquisition – it involves collecting files that are specifically related to the case under investigation.
- Sparse acquisition – identifying, preserving, analyzing, documenting, and then presenting the evidence.
2. Chain of custody and evidence handling procedures
Digital evidence falls under the same legal guidelines as other evidence. It involves the following:
- Integrity – ensuring the act of acquiring and collecting digital media doesn’t alter the evidence.
- Authenticity – the ability to confirm the integrity of information. The chain of custody from the crime scene through analysis and ultimately to the court, in the form of an audit trail, is an important part of establishing the authenticity of the evidence. Chain of custody provides a complete record of who accessed the file, at what time, and the sequence of activities performed on the evidence by any authenticated user.
3. Best practices for ensuring data integrity and reliability
To ensure the digital evidence legally admissible, you have to maintain data integrity and reliability – take a look:
- Creating a duplicate of an evidence file and perform analysis accordingly. It is imperative to limit every action on the original digital evidence file, or else it might not be accepted in court.
- The integrity and authenticity of digital evidence can be proved if the system is found to have generated a new hash value, which doesn’t match the original one. It is imperative to keep the file and your hard drive encrypted.
- Protect the digital evidence file with a strong passcode, so no one can access the sensitive data.
Analysis and Interpretation of Digital Evidence
1. Techniques for analyzing and interpreting digital evidence
- Acquisition – collecting digital evidence from a network or device, via imaging, logging, and live acquisition.
- Analysis – examining evidence to identify relevant information.
- Reporting – documenting findings of the analysis and presenting them in a clear manner for legal proceedings.
2. Common challenges and pitfalls in evidence analysis
- Encryption – it can be tough to access data on a device or network, if it is encrypted.
- Destruction – criminals often try to destroy digital evidence by wiping or destroying devices.
- Storage – the amount of data being stored on modern devices is huge, which makes it difficult for forensic investigators to search for relevant information quickly.
3. Reporting and presenting findings effectively
In digital forensics, reporting and presenting findings effectively is crucial to communicate the results of the forensic examination. It could include creating a detailed report of your findings, while providing testimony in court too.
- The report should be written in a way that is easily understandable by both technical and non-technical readers.
- The report should have a logical structure and be organized in a systematic manner.
- The report should provide a detailed explanation of the forensic methodologies employed during the investigation.
- The report should present the findings obtained from the forensic examination.
Conclusion
Digital forensics isn’t just limited to digital and computing environments – it has a much larger impact on society. Computers and electronic devices are being used in every aspect of our lives, which is why digital evidence is of paramount importance when it comes to solving crimes and other legal issues. In a world where we are connected by various devices, they generate massive amounts of data. Many devices log all actions performed by their users, as well as autonomous activities performed by the device, such as network connections and data transfers. Be it data theft and network breaches, online fraud, identity theft, violent crimes such as burglary, assault, and murder, and even white collar crimes, digital evidence plays an integral role in catching the culprit. Different types of digital forensics are utilized to ensure the perpetrators are brought to justice.