Learn key steps in malware analysis during digital forensics investigations, covering essential techniques and tools for effective forensic analysis.
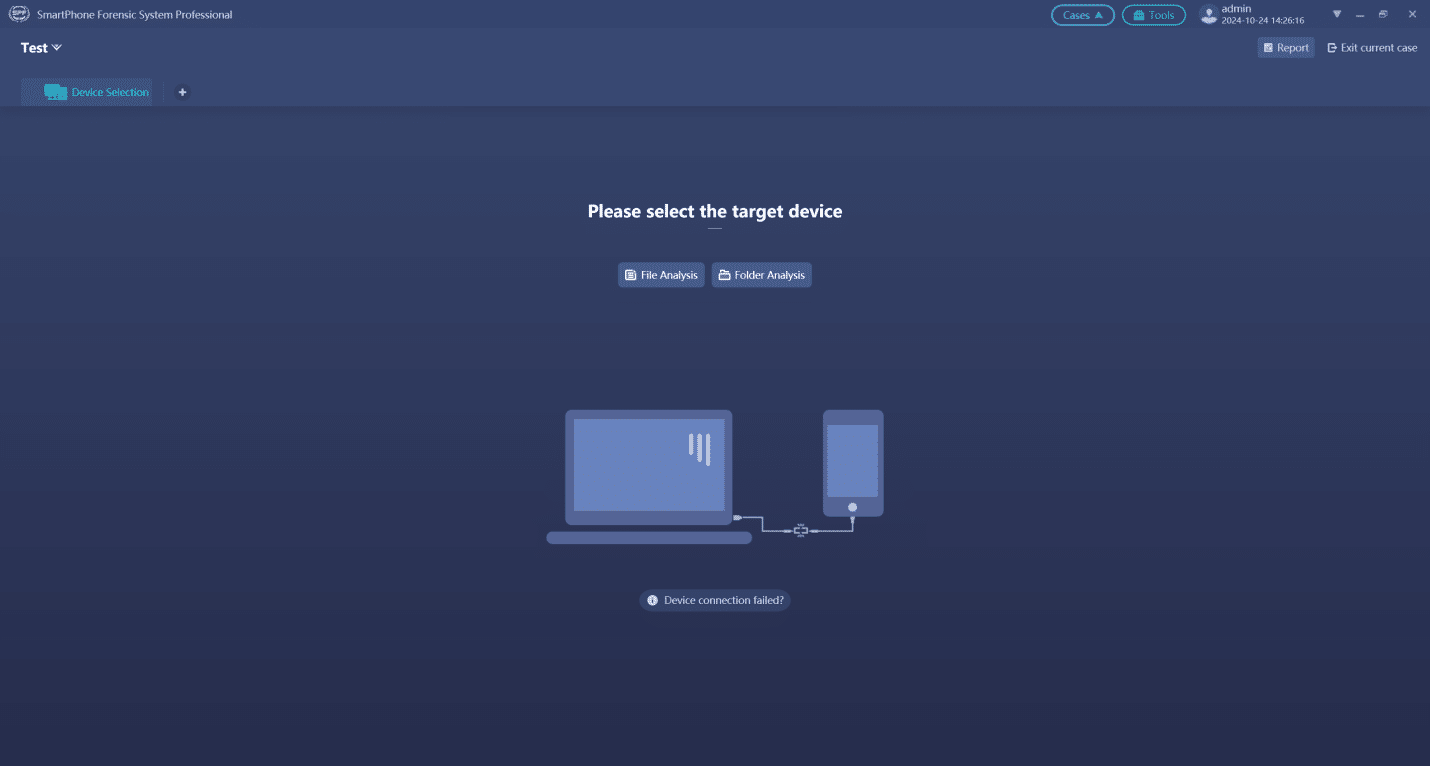
This article is talking about the steps to identify a mobile phone by SPF Pro when disconnected the internet.
Discover the crucial forensic imaging tools and software that enhance accuracy and efficiency in digital investigations, ensuring compliance and reliability in the field.
Enhance your investigative skills with our guide on the top 6 computer forensics skills essential for every digital investigator, ensuring thorough and compliant analyses.
Explore the best data carving tools essential for digital forensics, enhancing your ability to recover and analyze digital evidence effectively.
Explore the difference between file carving and metadata recovery, which facilitates precise forensic analysis and evidence recovery.
Explore how Envista Forensics leads with innovative digital forensic solutions, enhancing forensic investigation and data recovery for businesses worldwide.
Exploring the security of WhatsApp: Is WhatsApp safe for everyday use and private communications? Find out from a digital forensics perspective.
Explore the top five database encryption techniques essential for securing business data and ensuring compliance with industry standards.
Uncover the distinct roles and impacts of data acquisition and data logging in various industries, emphasizing the importance of each for data management.
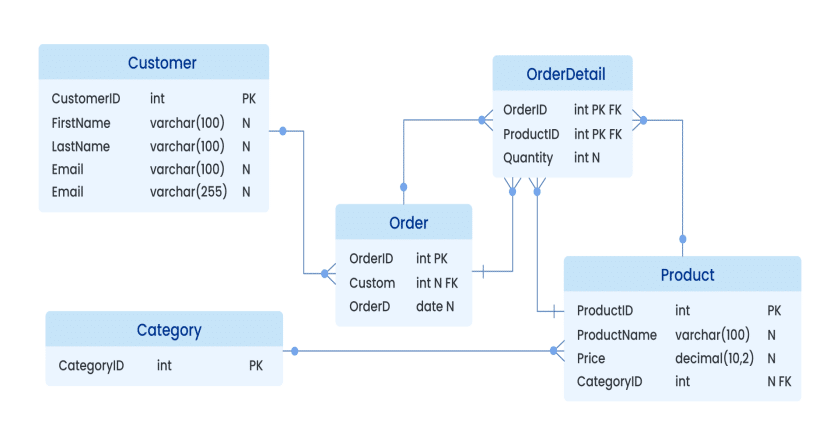
In this article, we are introducing a step-by-tep guide to use SPF Pro on database forensics in pyramid scheme cases.
Discover the essential differences between database schema and database model, understanding their roles in database structure and functionality