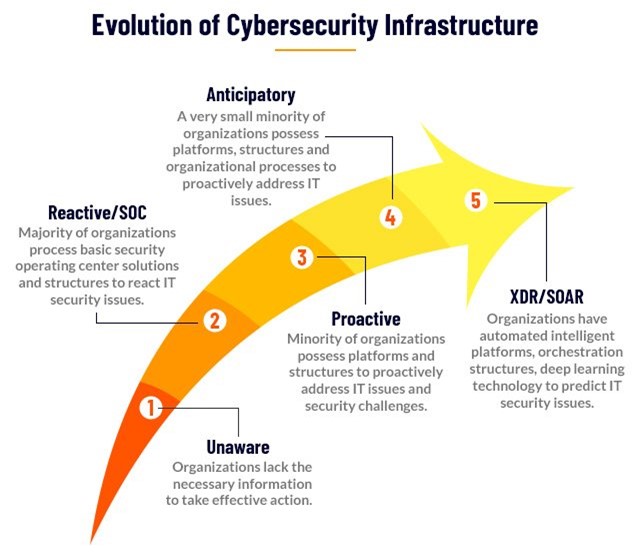
Digital Detective: Mobile Device Forensics in the Cyber Age

Introduction
With the ever-evolving cyber age, digital detectives have become a significant force fighting off cyber attacks daily. Since technology is advancing and always will, the schemas of malicious actors change accordingly, demanding more sophisticated knowledge about digital forensics. Digital detectives have potent skills and modern tools armed, standing on the front lines of a ceaseless technological competition.
The core of their responsibilities is the crucial task of mobile device forensics. Mobile device forensics is essential when solving cybercrimes as mobile devices store much information, from communication patterns to the behaviour with apps and the history of locations; all the details are necessary for completing a full image of a cybercrime investigation. By mastering this specialized area, digital detectives can obtain evidence, study it, and interpret pieces of proof on track in a cyberattack, therefore assisting them in identifying and apprehending cybercriminals.
This article outlines the evolution of cyber threats, emphasizing how digital detectives are critical in dealing with them. It illuminates the significance of mobile device forensics as a medium in the endless pursuit of justice in cyberspace, showing how promising innovations sit alongside those leading the digital detective race.
Evolution of Cyber Threats
Cyber threats have formed a highly dynamic and successively changing field in which it is developing with irrepressible talents of ‘Cyber criminals’—the overwhelmingly complicated background of the digital age. A significant transformation is underway, with a noted move in emphasis – mobile devices seem to be increasingly becoming the primary target of malicious actors.
Mobile devices appeal to cybercriminals because they provide constant Internet access and numerous apps that carry plenty of sensitive data. The information security or fraud detection department can view this as mobile devices are increasingly incorporated within individual and business lives; they have become more attractive approaches for cybercrime, from data breaches to electronic purse thefts.
Mobile devices no longer have such a simple role as storing valuable information; they are access points to integrated ecosystems and, hence, perfect targets for those who would compromise digital security. Since the development of cyber threats, there has been a highly sophisticated and versatile variety of attacks that are carefully designed with mobile platforms in mind, from malware up to phishing, through application-based exploits.
As cyber threats constantly change their forms, it is evident that mobile devices are considered primary targets, which also means digital criminals, which shows how adaptive and resourceful they are.
Case Studies
The three impactful cases are cited, which prove the application of mobile device forensics in solving complicated cyber crimes and thus highlight how such a particular disciplinary approach was crucial for unravelling intricate digital situations to improve cybersecurity further.
San Bernardino iPhone Encryption Battle
2016 became the point of no return for court fights about whether it was possible to unlock an iPhone that belonged to one of the shooters during the San Bernardino shooting. This case is where privacy versus national security issues proved far too sensitive. The emphasis was then on the encryption of the iPhone, which raises the question of whether digital evidence could be understood from strongly protected devices (Lowell, 2016). digital forensics experts did succeed in decrypting the iPhone depending on mobile forensics, which played a crucial role and was a lesson learned everywhere in this volatile landscape of national security investigations.
Boston Marathon Bombing Investigation
The 2013 Boston bombing was one such case where investigators used mobile device forensics to find out what happened before the attacks. Analyses of victims’ smartphones revealed communication records and location data about these suspects (Tapia & LaLone, 2014). In particular, during this complete analysis, it was essential to recreate the time frame of crime.
Operation Aurora Cyber Espionage
The 2009 Operation Aurora case is the cyber espionage on big IT corporations, which makes it a subject of mobile device forensics tools due to response mechanisms against these more developed and specialized patterns of security breaches (Adkins, 2013). However, this case also shows mobile device forensics that are not limited to criminal investigations and may help fight on a big scale and highly developed cyber threats. It discusses how this forensic science discipline could be among the piers to advance towards combating cyber-espionage and fortifying security defenses.
Analysis of the Role of Mobile Device Forensics
The pivotal factors that place mobile device forensics as the cornerstone in addressing cybercrimes and security incidents include:
First, when the investigators extract and analyze data from smartphones, it gives them a complete picture of digital activities committed by suspects. A reasonable timeline involving communication patterns, how applications were used, and the geo-location information could help track down individuals suspected of being involved in cybercrimes.
Second, the fact that forensics for mobile devices can reconstruct deleted or encrypted data is invaluable. Restoration of deleted files, decryption of the messages or access to hidden applications – this forensic analysis increases an investigatory possibility and accuracy in achieving essential proof that criminals previously concealed.
In addition, proactive threat detection is present in some mobile forensics tools‘ real-time monitoring features. This aggressive mode helps characterize mobile device forensics’ flexibility in tracking changing security issues, where it is the most crucial interference and reduction of cyber threats.
Mobile Forensics Tools
Nowadays, digital forensics is a science that uses dfir tools and technologies to explain the intricacies of mobile phones when decoding them to recover essential data during investigations.
Leading Mobile Forensic Software Solutions
1. Cellebrite UFED
Cellebrite UFED has been a significant player in the mobile forensics industry and provides an all-in-one data extraction and analysis solution. It offers a vast range of smartphones and operating systems, making it quite versatile for investigators. It also offers the following capabilities – call log, messages, and app data extraction, along with advanced functionality such as deleted file recovery and passcode bypass.
2. SPF Pro (Smartphone Forensics System Professional)
SPF Pro is a comprehensive mobile forensic platform developed by SalvationDATA, which allows data extraction recovery analysis and report exporting of information from different kinds of mobile devices. Important aspects are the broad support for existing popular brands of smartphones and applications, an almost universal matching with any operating system used by mobile phone producers, and good multitasking that can effectively handle up to 8 different devices physically and logically in terms of management.
3. Oxygen Forensic Detective
Oxygen Forensic Detective is famous for its flexibility and powerful features in solving mobile device forensics. It supports a broad array of mobile phones, applications and cloud services. It contains ordinary data such as call logs and messages but includes more sophisticated information like geolocation data and Wi-Fą connections. Its broad approach to data enables it to devise elaborate timelines and comprehend user activities, making it the best. Contact to apply for a Free Trial now!
4. MSAB XRY (Xtract, Recover, Yse)
MSAB XRY is a robust mobile forensic tool that can acquire and analyze data from different mobiles. MSAB XRY supports several device models and operating systems; it can deal with challenges related to mobile forensics. The data extraction includes logical and physical password bypass capabilities and advanced analysis in decoding various data formats. Click here to Update your software here!
Key Features and Capabilities Crucial for Mobile Device Investigations
1. Abundant Device and App Support
Supporting various smartphone brands and popular applications is essential for effective digital forensics software. This allows investigators to obtain pertinent data from a wide range of devices, considering that the landscape of mobile technology is ever-changing.
2. Efficient Data Extraction and Recovery
Mobile forensics focuses on the effectiveness of data extraction and retrieval. Tools such as SPF Pro’s multitasking features allow dealing with various devices simultaneously, thus quickening the data extraction. Such efficiency is what investigators need in time-sensitive cases.
3. Intelligent Data Extraction Solutions
SPF Pro is an excellent example of a mobile forensic tool that keeps changing, as seen in intelligent data extraction tools. Such solutions define the character of data and indicate how best to get it. For instance, this level of intelligence simplifies the investigation because investigators can focus on relevant information much more quickly.
4. Real-time Evidence Collection
For instance, the real-time evidential gathering ability, like a file explorer in SPF Pro, gives mobile forensics a touch of dynamism. When incidents happen, digital forensics experts can access and gather evidence data from cell mobile devices. Such an attribute is beneficial when a timely action or reaction is crucial.
5. Intelligent Analysis of Sensitive Data
Tools, such as SPF Pro for mobile forensics, actively monitor and notify investigators when sensitive data is accessed. It includes keywords, apps, URLs, phones, MD5, and flexible properties. Intelligent analysis of sensitive data will enhance the proactive detection of possible threats, thus enabling investigators always to have the upper ground whenever considering evolving security challenges.
Investigative Techniques
Aside from software solutions, it relies on solid investigative techniques to ensure a successful mobile forensics investigation. These include:
1. Data Acquisition Methods
Choosing the proper method to obtain data is imperative in mobile forensics investigations. It is based on the status of a device and the goals of an investigation to use physical or logical extraction methods. Physical extraction provides a complete storage picture for locked or damaged devices. On the contrary, analytical extraction centres on specific data types; it is fast and precise for operational appliances requiring particular information.
2. Mobile Forensics Process
Investigators follow a process referred to as systemic mobile forensics that will take them from evidence collection through analysis and reporting. It starts from large-scale data acquisition and proceeds to the detailed analysis of the patterns and relationships within the extracted material. The final phase involves the preparation of detailed reports, reporting on findings and methodologies. This structured method enhances the reliability and precision of results so that an investigator can meet all the challenges related to digital evidence in a sound framework.
3. Preservation of Evidence
The preservation of evidence contributes to maintaining a level of integrity in data. Collected evidence is stored in facilities with adequate security measures like encryption and access control. This also involves the proper chain of custody paperwork. This complex, intensive log records the movement and processing of digital evidence, establishing its admissibility in judicial proceedings.
4. Timeline Analysis
To satisfy data timeline analysis, it is enough to point to the days when events happened. This approach gives a digital forensics expert background on all aspects of digital activities, enabling her to puzzle events together and understand behaviour. The temporal perspective enables researchers to identify the trends of causes and dependencies between various digital activities. Timeline analysis is critical due to its ability to determine what digital footprints users have captured on mobile phones.
5. Chain of Custody Management
In mobile forensics, ensuring the security and proper documentation of the chain of custody is critical. This practice can be seen as an elevated form of paperwork, documenting every time digital evidence is handled or passed on and where it is stored at each step in the investigative process. An effective chain of custody enhances trust systems in the investigative process because it ensures that evidence is admissible and has integrity when presented during legal proceedings.
Overall, the devices and technologies utilized by mobile forensics assist in retrieving critical evidence from these omnipresent devices typical of cyberspace. No means that online TV On the contrary, with some of the most progressive software solutions like Cellebrite UFED, SPF Pro, Oxygen Forensic Detective or MSAB XRY in tandem analyzing specific investigative procedures will help digital detectives to go through network channels connected with any further development of a practical mobile device forensics considerations enhancing cybersecurity.
Conclusion
In conclusion, in the maelstrom of rapidly changing cyber threats, teams of digital detectives parallel to law enforcement and computer security researchers become integral to preventing hacking cases. Most sophisticated tools and methods of investigation are used in mobile device forensics, which means that such people not only can find significant evidence on a piece of digital data necessary for proper detection but can also withdraw them concerning cyber criminals. Law enforcement agencies also offer legal guidelines and the opportunity to enforce laws so that they become legally punishable behaviors once threats are detected. On the other hand, cybersecurity specialists bolster defenses and install protective measures besides suggesting guidelines regarding new threats. By supporting collaborations, we build an invincible fortress of all our constantly changing cyber strategies essential for maintaining this interconnected world’s integrity. Thus, an integrated multi-faceted approach is a lighthouse that finally immunizes the digital landscape against all cyber threats to everyone’s advantage.