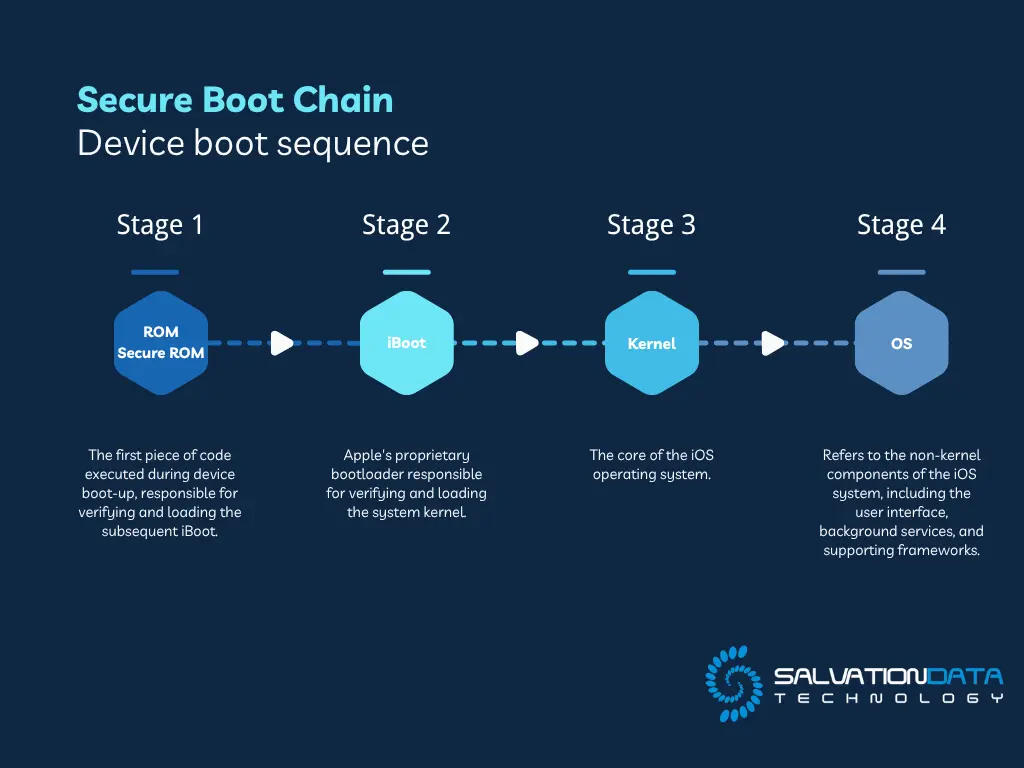
Checkm8 is a powerful, unpatchable exploit in Apple’s SecureROM that affects millions of devices, including iPhones and iPads up to the iPhone X. First disclosed by axi0mX in 2019, the Checkm8 exploit enables persistent low-level access for jailbreaking, security research, and forensic data extraction. Unlike typical software exploits, Checkm8 leverages a hardware-level vulnerability that Apple cannot fix through updates.
In this guide, you’ll learn how Checkm8 works, how it bypasses Apple’s Secure Boot Chain, and how to use Checkm8 safely for research and lawful analysis. Whether you’re exploring Checkm8 jailbreak methods or studying iOS security, understanding Checkm8 will deepen your knowledge of how hardware exploits can transform device access and analysis.